How to Securely Store Passwords in PowerShell
Storing passwords is a crucial part of any Windows user’s life. When it comes to storing the passwords for security purposes, storing them inside the text file is not good. However, it can be stored in a more secure manner, which is by using PowerShell. Such as, users can utilize the “SecureManagement” module to save or encrypt passwords securely in PowerShell.
This write-up will go through the complete procedure to securely store the passwords in PowerShell.
How to Securely Store Passwords in PowerShell?
Users can securely store the passwords:
Method 1: Store the Password in PowerShell
Securing a password while storing is very important. Users can secure the password in PowerShell by navigating through the provided instructions below.
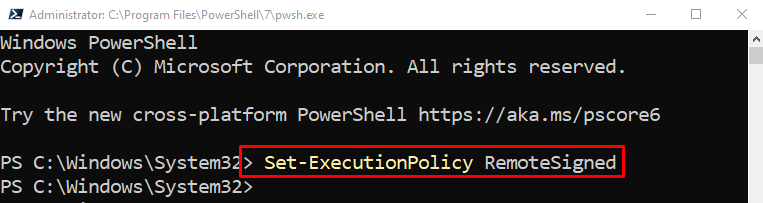
Step 1: Set Execution Policy Remote Signed
First of all, set the execution policy to “RemoteSigned” by executing the given command:
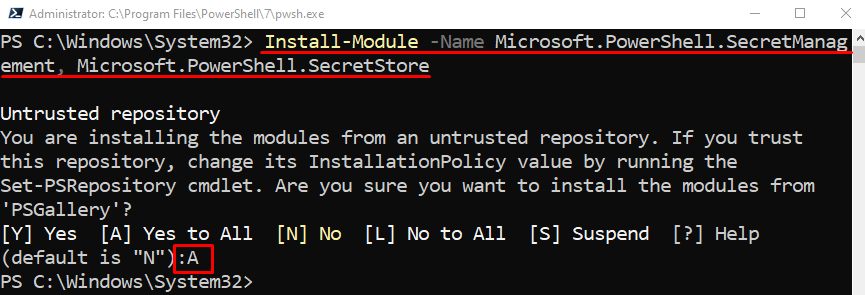
Step 2: Install the SecretManagement and SecretStore Module
Now, install the Microsoft “SecretStore” and “SecretManagement” modules. To do so, first, use the “Install-Module” cmdlet and specify the modules to be installed separated by commas:
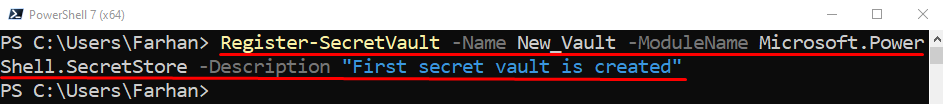
Step 3: Create Microsoft Secret Vault
After installing the modules, now, create the Microsoft Secret Vault. To do so, first, specify the “Register-SecretVault” cmdlet along with its name assigned to the “-Name” parameter. After that, specify the “SecretStore” module to the “-ModuleName” parameter. Lastly, use the “-Description” parameter and specify the description of the vault:
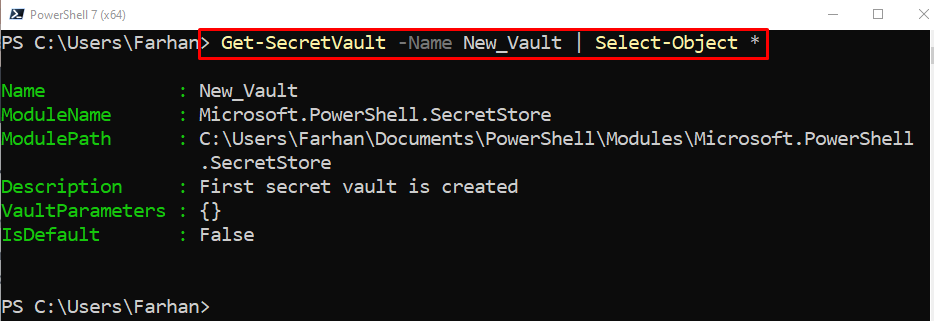
Step 4: Get the Newly Created Vault
To retrieve the newly created vault, simply use the “Get-SecretVault” cmdlet along with the name of the vault assigned to the “-Name” parameter. After that pipe the whole command to the “Select-Object” cmdlet followed by an asterisk:
Step 5: Create and Store a Password
Now, to create the password, first, place the “Set-Secret” cmdlet along with its name assigned to the “-Name” parameter. Then, assign the secret to the “-Secret” parameter. When the below command is executed, the prompt will require the user to type the password twice. Entering the password twice will securely store the password:
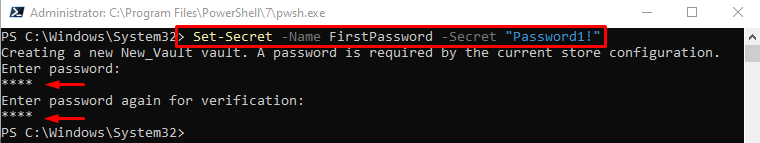
Step 6: Get the Secure Password
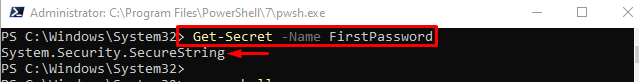
To get the securely stored password, first, place the “Get-Secret” cmdlet and assign the name of the password to the “-Name” parameter. It will not reveal the password, however, it will only tell whether the password is a string or integer:
To view the password simply place the “-AsPlainText” parameter at the end of the command:
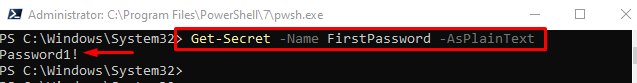
It can be observed that the password has been revealed in the PowerShell.
Method 2: Store Password in a Text Document
Another way of storing the passwords is inside the text file. To store the passwords inside the text files, navigate through instructions provided below.
Step 1: Ask the User to Provide Credentials
First, execute the cmdlet “Get-Credential”, to ask the user to type his/her credentials. Then, store the credentials to the “$credential” variable:
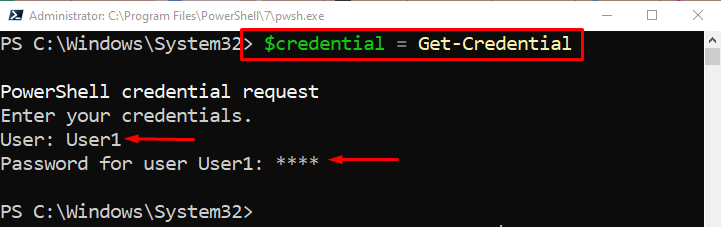
Step 2: Store the Encrypted Password in the Text File
Now, save the password retrieved from the user to the text file. To do so, first, concatenate the password stored variable with the “Password” keyword and pipe it to the “ConvertFrom-SecureString” cmdlet. After that, again use the “|” pipe and specify the “Set-Content” cmdlet having the text file path assigned to where the password will be stored:
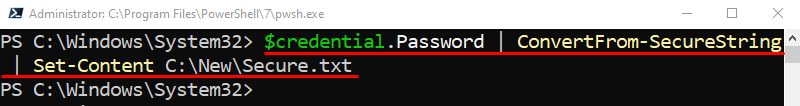
Get the Encrypted Password
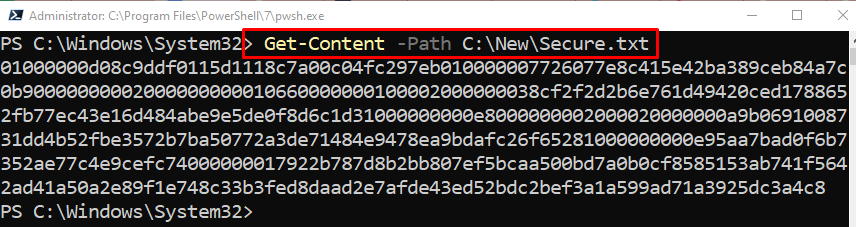
Verify whether the password was stored in the text file or not by executing the “Get-Content” cmdlet along with the “-Path” parameter having the text file assigned to it:
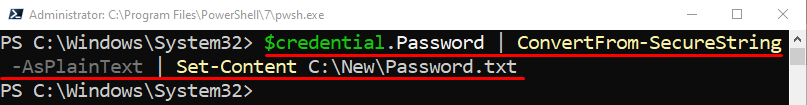
Step 3: Store the Password as a Plain Text
In order to store the password as a plain text, simply add the “-AsPlainText” parameter along with the “ConvertFrom-SecureString” cmdlet:
Get the Stored Password
To check whether the password was stored as a plain text or not, simply execute the below command:
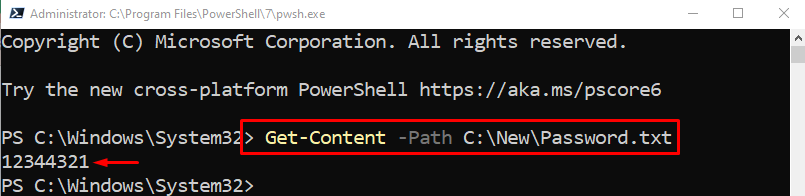
Conclusion
To securely store a password in PowerShell, first, set the ExecutionPolicy to RemoteSigned. Then, install the “SecureManagement” and “SecretStore” modules. After that, create the vault and store the passwords inside it. This article has provided a detailed procedure to securely store passwords in PowerShell.
Source: linuxhint.com
