Stealth Scans With Nmap
This tutorial describes different techniques to execute stealth scans with Nmap.
Stealth scan techniques are implemented to bypass firewalls or discover hosts alive while remaining undetected.
Nmap offers a variety of flags and options to execute different stealth scan types, most of which are explained in this article. They are easy to implement and constitute a nice learning process on IP packets.
After reading this content, the reader will enjoy a better understanding of network packets and communications while acquiring deep practical knowledge on stealth scans with Nmap.
All instructions in this tutorial contain screenshots, making it easy for all readers to understand how they are executed and their outputs or results.
Brief Introduction to Stealth Scans
Usually, firewalls detect establishing or established connections.
TCP sends packets trying to establish a connection with the target (Gathering information in the process). This activity may be blocked and logged by the firewall to be reported to the administrator.
Suppose the user has root privileges by default. In that case, Nmap runs stealth scan techniques consisting of SYN (Synchronization) packets and RST packets interrupting the connection after the first reply from the destination.
Users can prevent firewalls from detecting the scan by interrupting the brief interaction at a time and canceling the connection process before sending an ACK reply.
As you can see in the figure below, a regular TCP scan consists of an initial SYN (Synchronization) packet from Nmap (PC1) requesting the target (PC2) to synchronize a connection. If the targeted port is open, the target replies SYN+ACK (Acknowledgment and Synchronization) packets confirming the SYN reception and the synchronization to Nmap, and Nmap sends ACK (Acknowledgment) packets as a reply to the target’s SYN.

The following figure shows a stealth scan with SYN packets. As you can see, the final acknowledgment (ACK) packet sent by PC1 (Nmap) is replaced with an RST packet, interrupting the connection to bypass firewalls (Intrusion Detection Systems and custom firewalls will detect stealth scans).
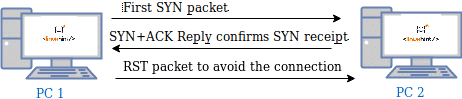
Nmap TCP SYN (Stealth) Scan Techniques
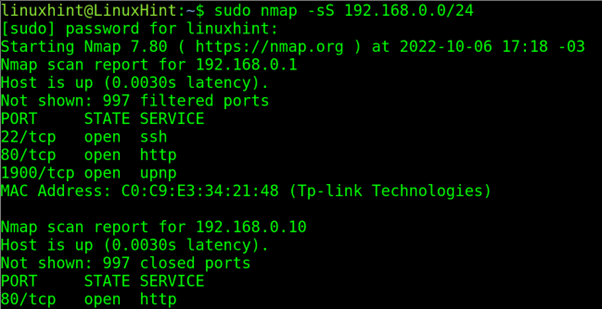
To execute an SYN or stealth scan like the one depicted in the previous second figure, the user must implement the –sS (SYN) flag. This option will reset the connection before its established.
Note: The SYN scan requires root privileges; use the sudo command.
In the following example, a stealth scan is executed against the network 192.168.0.0/24:
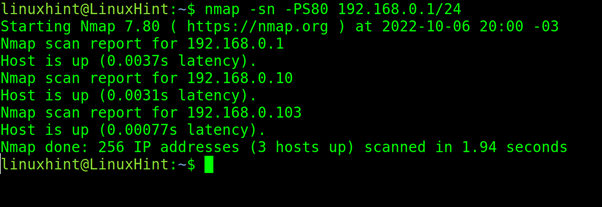
TCP SYN Ping Scan
The -PS flag allows you to launch SYN ping to discover alive hosts in a stealthy way.
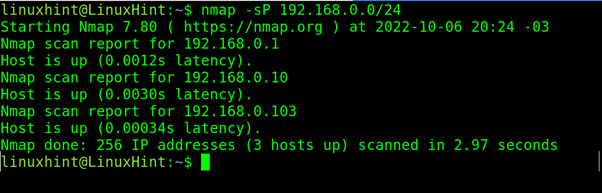
The -sP flag will also run a no ping scan without a port scan.
Nmap NULL scan
Despite sending an RST packet preventing the connection from being logged, an SYN scan can be detected by firewalls and Intrusion Detection Systems (IDS). There are additional techniques to carry out more stealthy scans with Nmap.
Nmap works by analyzing the packet’s responses from the target, contrasting them with protocol rules, and interpreting them. Nmap allows forging packets to generate the proper responses revealing their nature, for example, to know if a port is closed or filtered by a firewall.
The following example shows a NULL scan that does not include SYN, ACK, or RST packets.
When executing a NULL scan, Nmap can interpret three results: Open|Filtered, Closed, or Filtered, where:
- Open|Filtered: Nmap can’t determine if the port is open or filtered by a firewall.
- Closed: The port is closed
- Filtered: The port is filtered.
In the next practical example, the user uses the -sN flag to run a NULL scan:
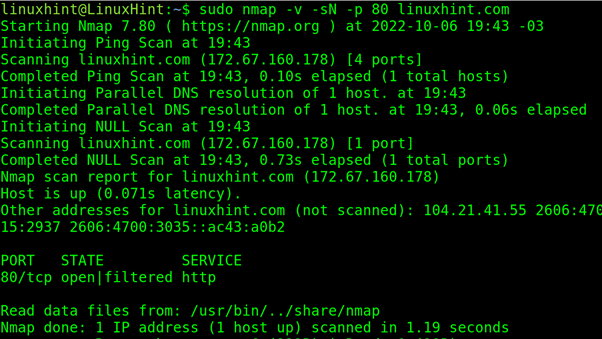
As shown in the following example, you can add the option -sV to discover if the port portrayed as Open|Filtered is actually open, but adding this flag may result in easier scan detection by the target, as explained in Nmap’s book.
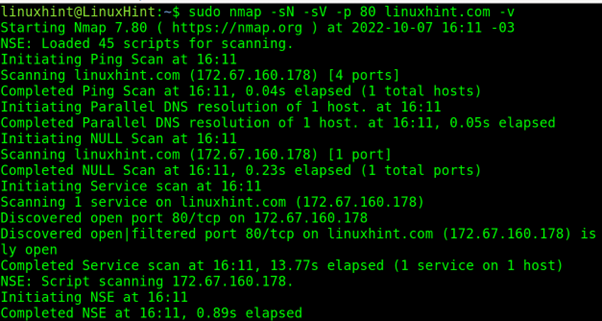
- nmap = Calls the program
- -v = Instructs Nmap to scan with verbosity
- -sN = Instructs Nmap to run a NULL scan
- -sV = Version detection
- -p = Prefix to determine the port to scan.
In some cases, firewalls block SYN packets. In such a case, the user can send a packet with flags SYN/ACK to bypass firewalls that don’t block SYN/ACK packets.
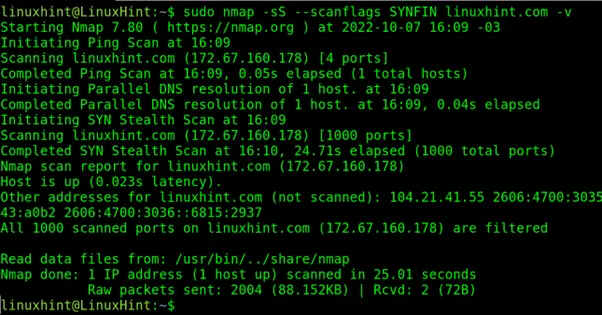
Some packets are not blocked in SYN with ACK packets and also allow the combination of SYN with other headers, the SYN/FIN header is one of them.
The following scan type will send SYN and FIN headers. This scan type has a low chance of remaining undetected.
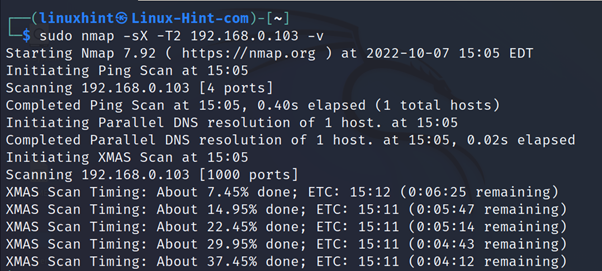
Nmap Xmas Scan
Xmas scan was considered a stealth scan technique analyzing responses to Xmas packets to learn the type of remote system.
Each operating system or network device replies to Xmas packets in a different way revealing information, such as the operating system and port states.
Xmas is an old scan technique; today, many firewalls and Intrusion Detection Systems can detect Xmas. It is not recommended to rely on them as a stealth technique.
Comparison between TCP SYN stealth scan and TCP “Connect Scan”:
Normal TCP Communication
- -“Hey, can you hear me? Can we meet?” (SYN packet requesting synchronization)
- -“Hi!, I see you!, we can meet” (Where “I see you” is an ACK packet, and “we can meet” is a SYN packet)
- -“Great!” (RSTet pack)
SYN Stealth communication
- -“Hey, can you hear me? Can we meet?” (SYN packet requesting synchronization)
- -“Hi!, I see you!, we can meet” (Where “I see you” is an ACK packet, “we can meet” is a SYN packet)
- -“Sorry, I sent a request to you by mistake, forget about it” (RSTet pack)
The second example above shows a SYN connection, which does not establish a connection in contrast to a TCP connection or Connect Scan. Therefore there is no log on the second device about a connection, nor is your IP address logged.
Other Nmap Flags (No Stealth)
In addition to the stealth scan techniques, we decided to describe some different flags.
It is important to clarify that the following flags below are not stealthy.
The -O flag can detect the target operating system, as shown in the following screenshot:
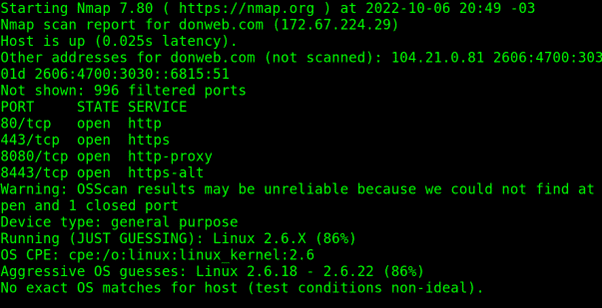
As you can see in the previous screenshot, the target probably has Linux with kernel 2.6.x; according to the report, detection conditions were difficult.
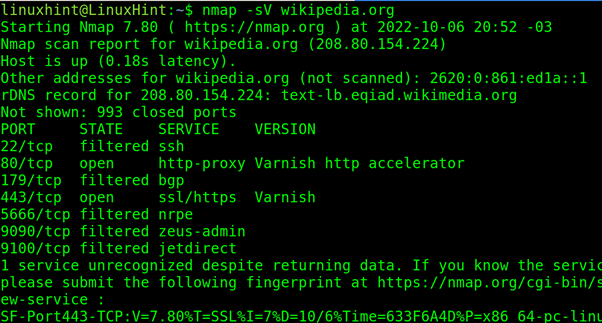
The following example tries to learn the software version (-sV) listening behind ports. As you can see, Varnish was detected.
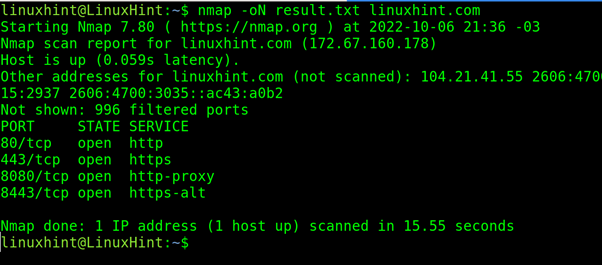
The -oN flag creates a file with the results of the scan.
In the following example, the user implements the -oN flag to create the file “results.txt” with the scan output.
That’s all about stealth scan methods. You can test them with an Intrusion Detection System like Snort to see their effectiveness before different detection rules.
Conclusion
As you can see, Nmap offers different stealth scan techniques. They all are easy to implement, and the technique is easy to understand if the user knows networking basics. Readers with minimal experience can reproduce the given practical examples without major difficulty. It is highly recommended to apply the example additionally to the reading.
All the given instructions are valid for all Linux distributions.
Thank you for reading this tutorial explaining how to run stealth scans with Nmap. Keep following Linux Hint for more networking and security professional content.
Source: linuxhint.com
