How to Modify Secrets with AWS Secret Manager Using AWS Console?
Quick Outline
This article presents information on the following aspects:
- What is AWS Secret Manager?
- How to Modify Secrets with AWS Secret Manager Using AWS Console?
- Bonus Tip: Key Features of AWS Secret Manager
- Conclusion
What is AWS Secret Manager?
AWS Secret Manager is used to encrypt and secure the confidential information of the application. Such confidential information includes Database credentials, OAuth tokens, and API Keys. This information is referred to as “secrets”.
AWS Secret Manager is extremely useful for developers when they do not want their credentials to be stored in the source code for security purposes. These secrets are accessed by making a runtime call to the Secret Manager. By using the Secret Manager, developers can prevent the possible compromise on the security of applications.
How to Modify Secrets with AWS Secret Manager Using AWS Console?
Users can improve the security of the secrets by using an automatic rotation schedule and deploying these secrets in multiple regions. With AWS Secret Manager, users can store and secure secrets either in the key-value pair or JSON document. It is worth noting here that the JSON document helps the user to manage secrets of size 64 KB.
Learn more about storing Amazon RDS Credentials in AWS Secret Manager by referring to this article: “How to Store Amazon RDS Credentials Using Secret Manager”.
There are several different ways in which a secret can be modified. Some of them are as follows:
- Method 1: Update the Value of the Secret
- Method 2: Change the Encryption key of the Secret
- Method 3: Change tags of the Secret
- Method 4: Delete Secret
- Method 5: Restore Secret
- Method 6: Change the Description of the Secret
Method 1: Update the Value of Secret
When the user updates the value of the Secret, AWS replaces the label of the secret with “AWSCURRENT”. The old version of the Secret is accessible which has the label “AWSPREVIOUS”.
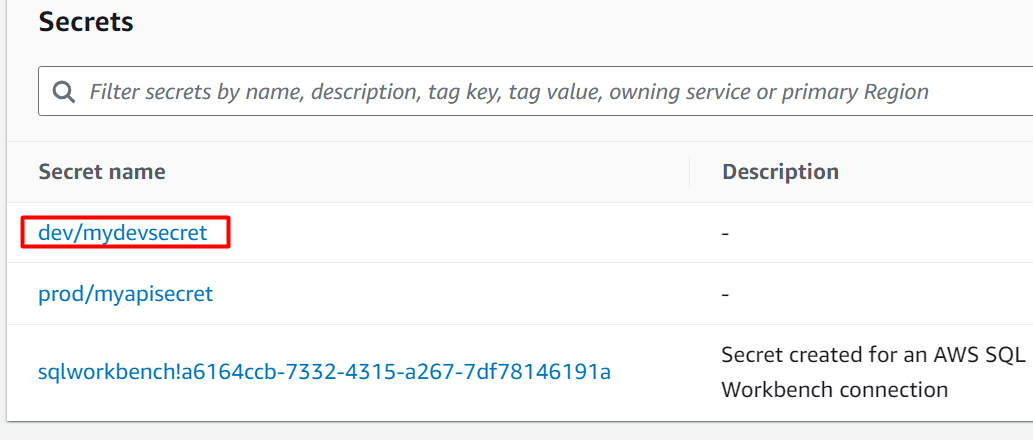
On the AWS Secret Manager Dashboard, click on the name of the secret:
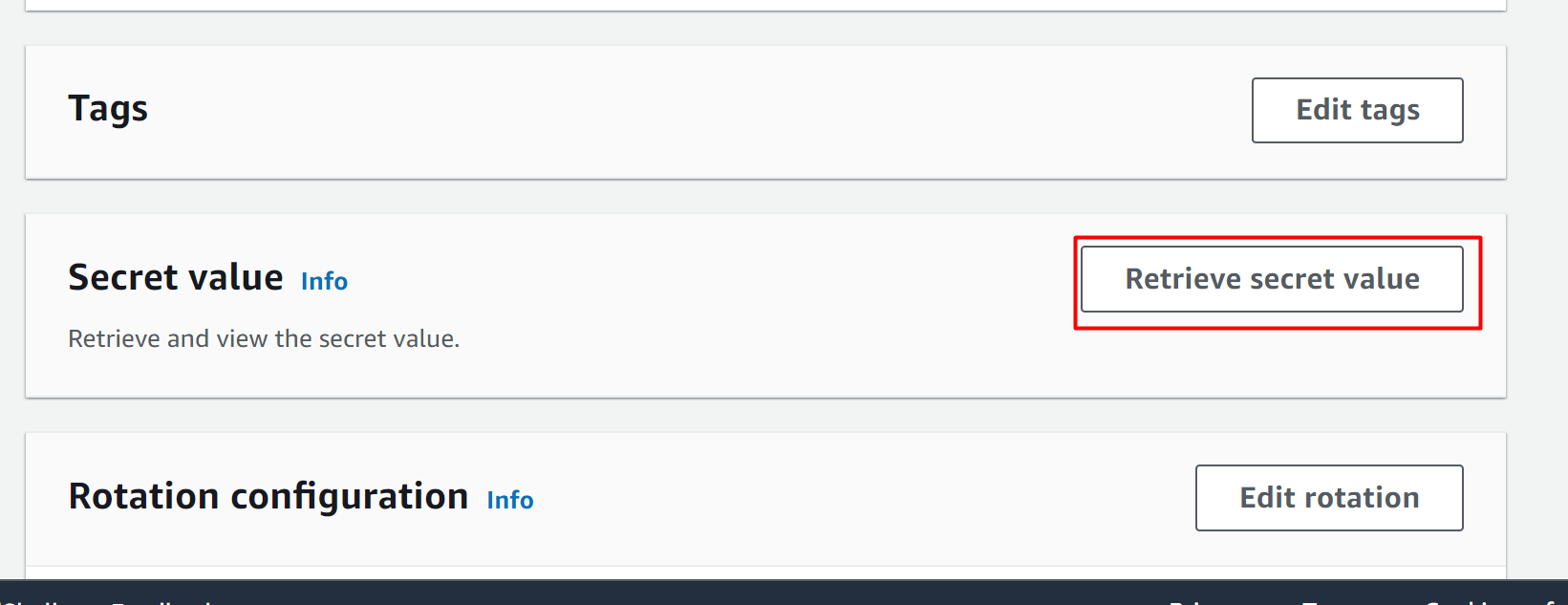
Scroll down the interface and locate the Secret Value section. Here, click on the “Retrieve secret value” button:
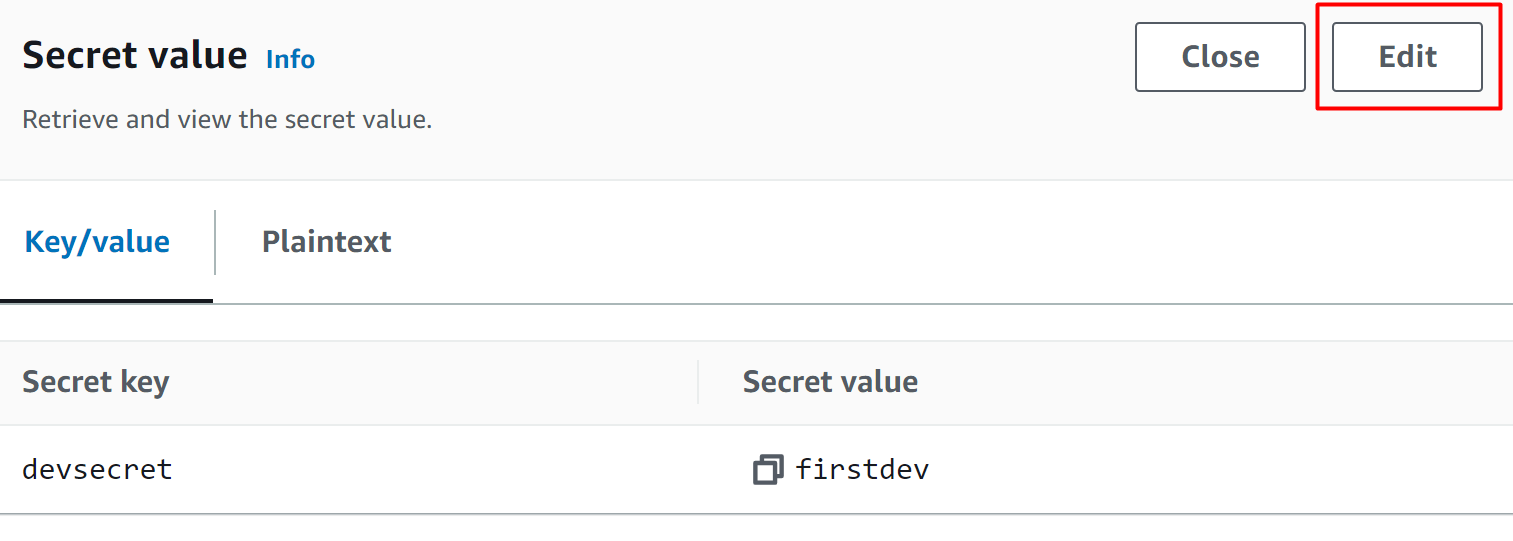
The following interface will be displayed. Click on the “Edit” button to change the value of the secret:
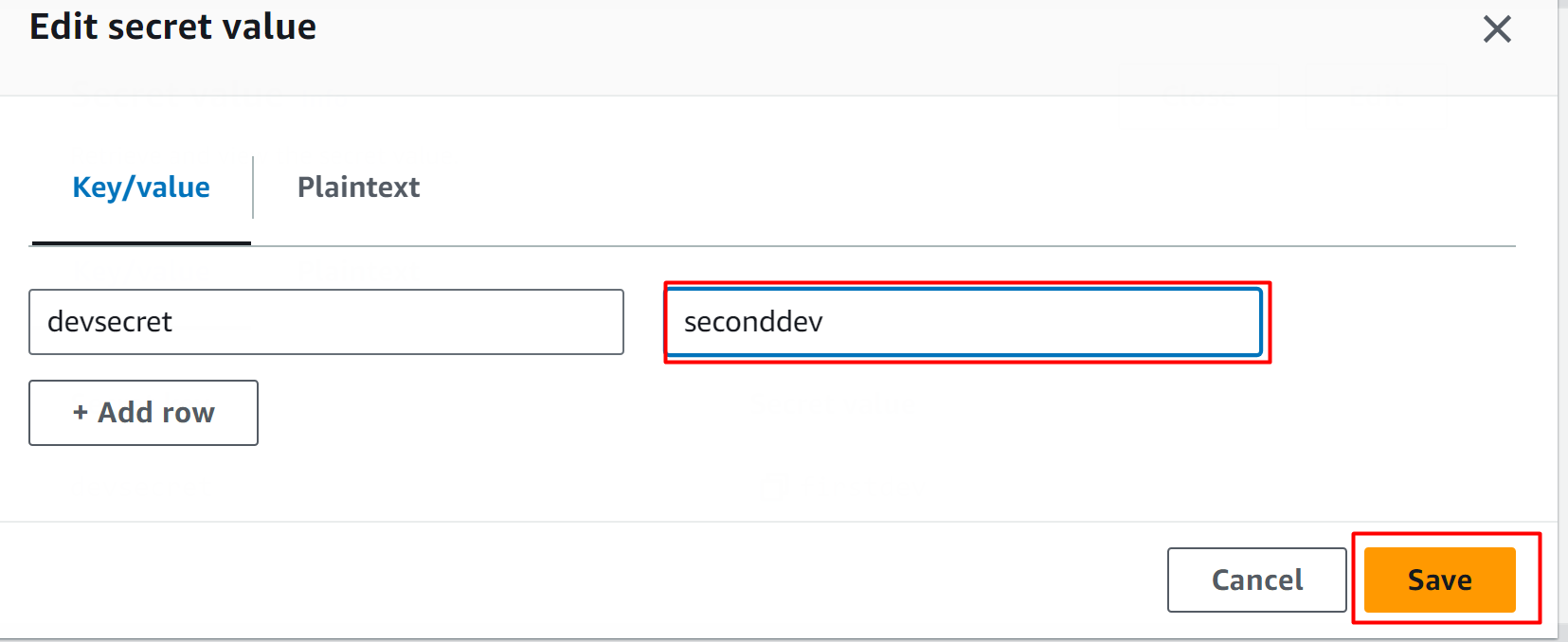
A pop-up window will be displayed to you. On this window, edit the value of the secret and click the “Save” button:
The secret value has been successfully updated:
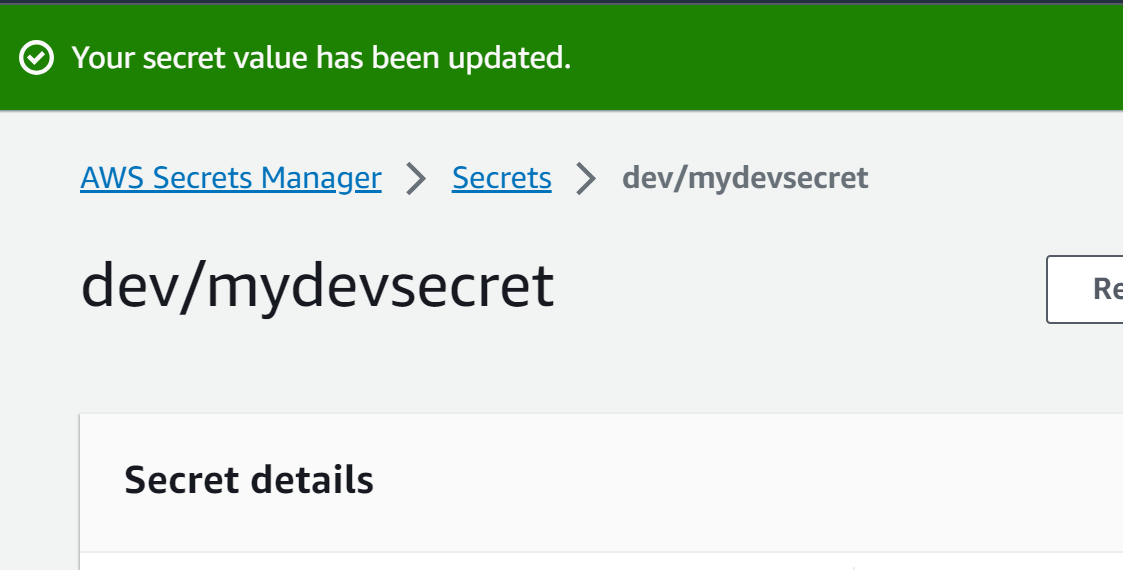
Method 2: Change the Encryption Key Value of Secret
Encryption enhances security and filters the access of secrets. Secret Manager uses the Envelope Encryption with AWS KMS for the secrets’ protection. By default, AWS provides aws/secretmanager managed key which is a recommended practice. However, users can also use customer-managed keys.
On the AWS Secret Manager dashboard, choose the secret for which you want to modify the Encryption Key value:
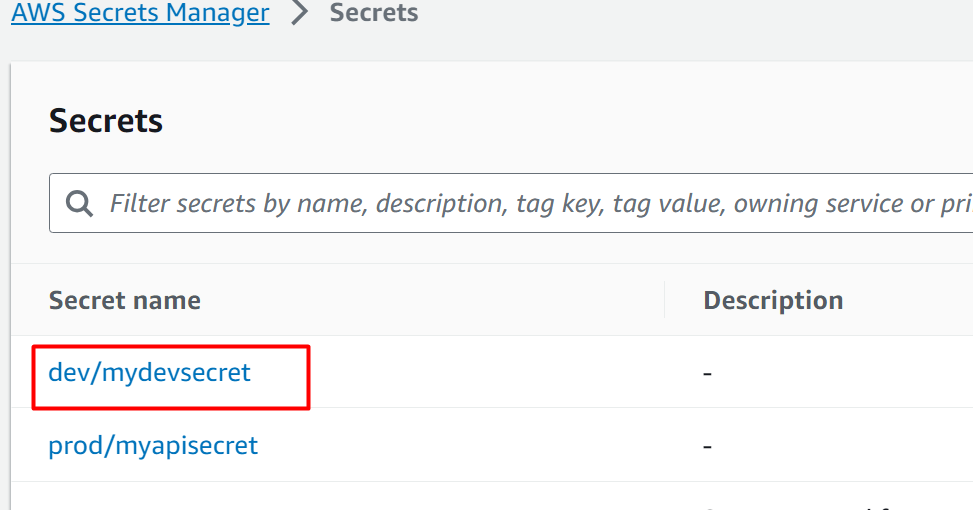
From the interface displayed, click on the “Actions” button. This will display a drop-down menu. Click on the “Edit encryption key” option:
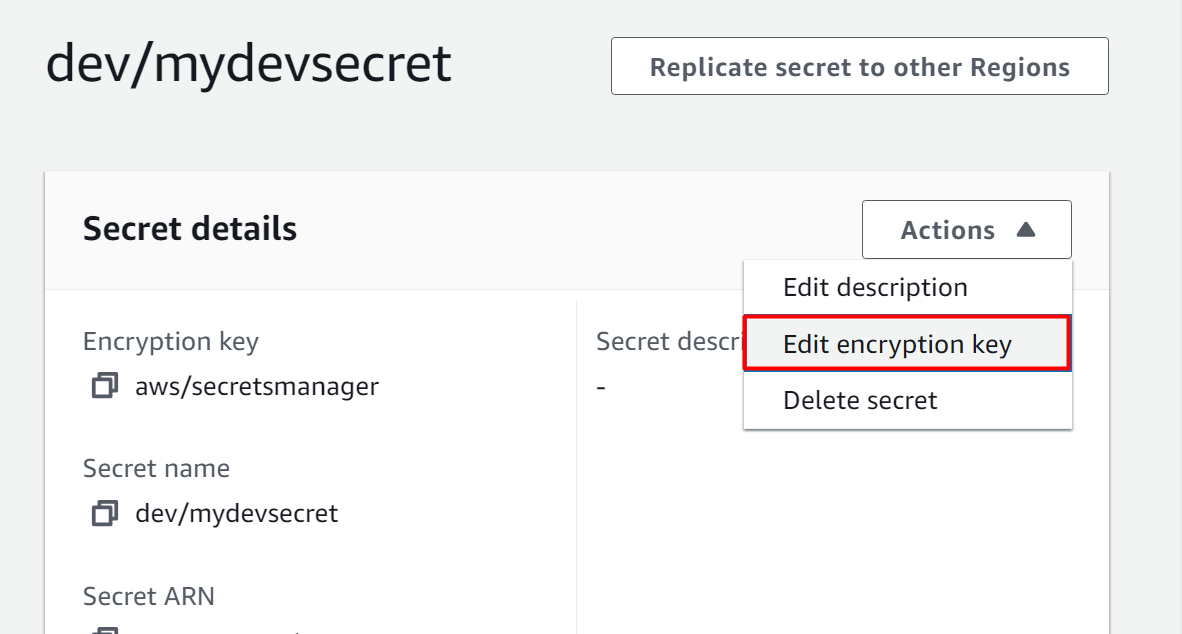
On the Edit encryption key window, the user can either select a key or create a new one by clicking the “Add new key” option. After modifying the encryption key value, click on the “Save” button to apply changes:
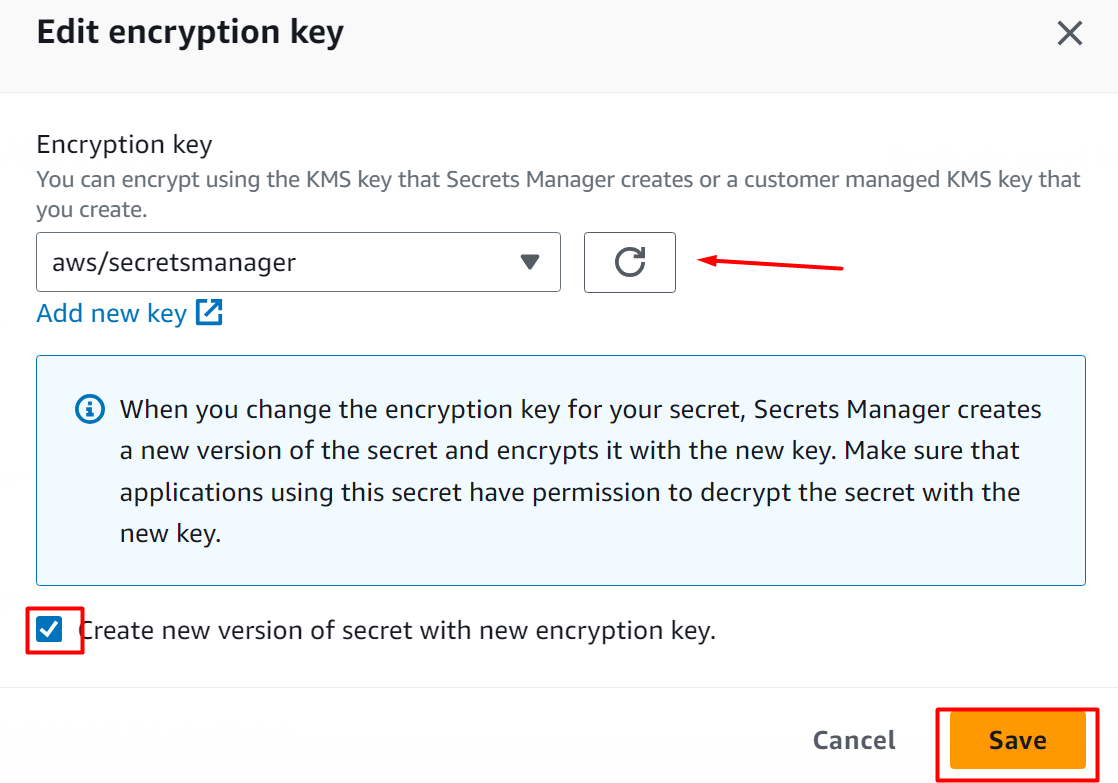
AWS will display a confirmation message that indicates that the value has been successfully updated:
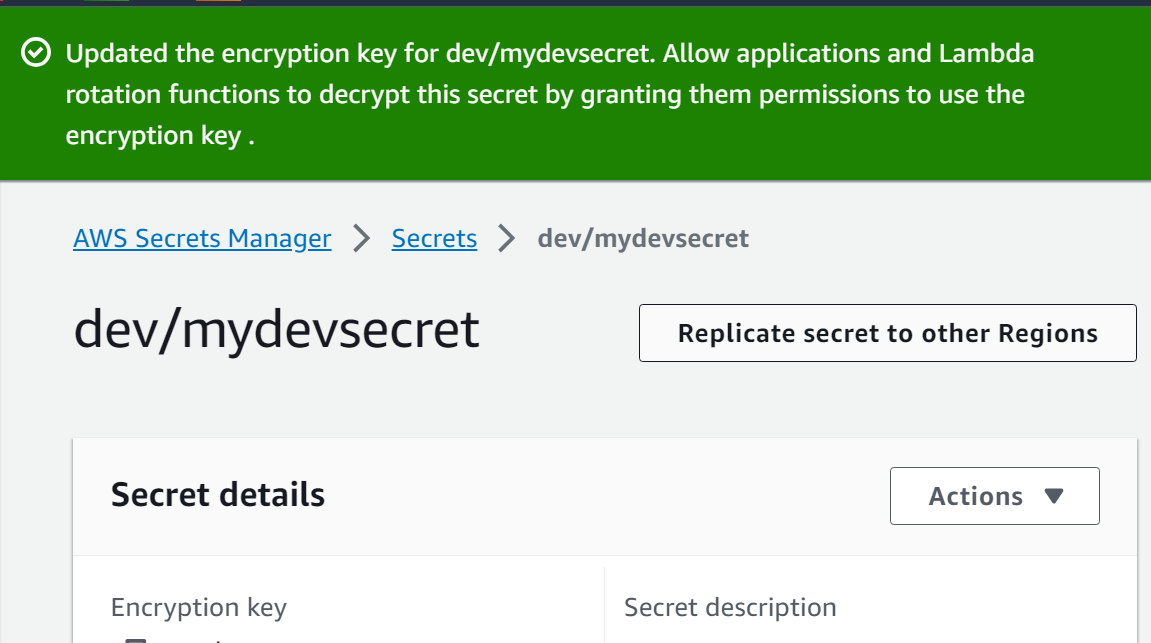
Method 3: Change Tags of a Secret in AWS Secret Manager
Tags are the labels consisting of a key which is user-defined and an optional value. With tags, user can easily manage, search, and filters the AWS resources. Tags associated with the secrets can also be used to grant or deny access. Note that the AWS follows a standard for tagging the resources. it is recommended that the user should use a standard naming scheme and should avoid storing sensitive data in the tags.
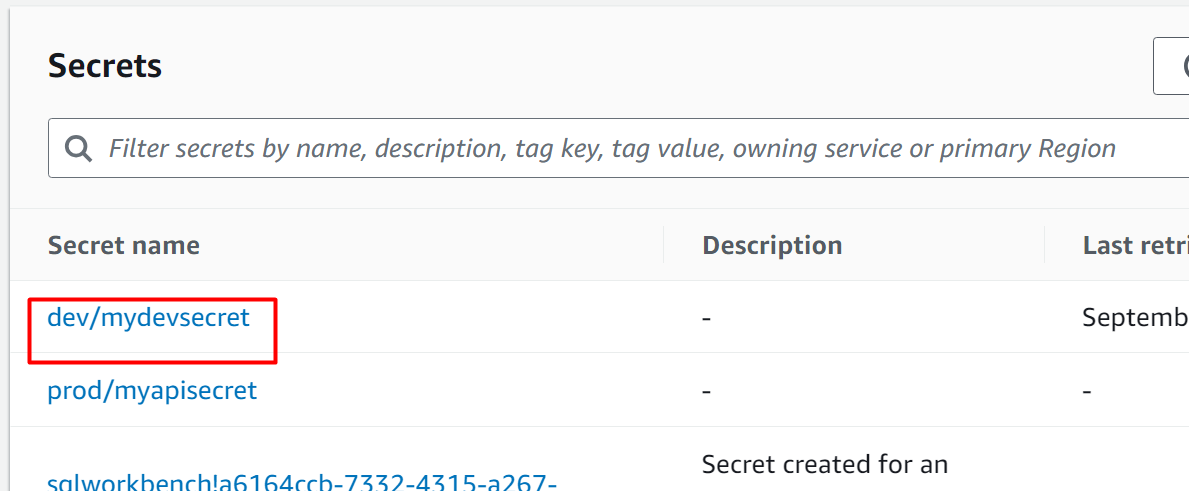
To change the Tags of a Secret, tap the secret from the AWS Secret Manager:
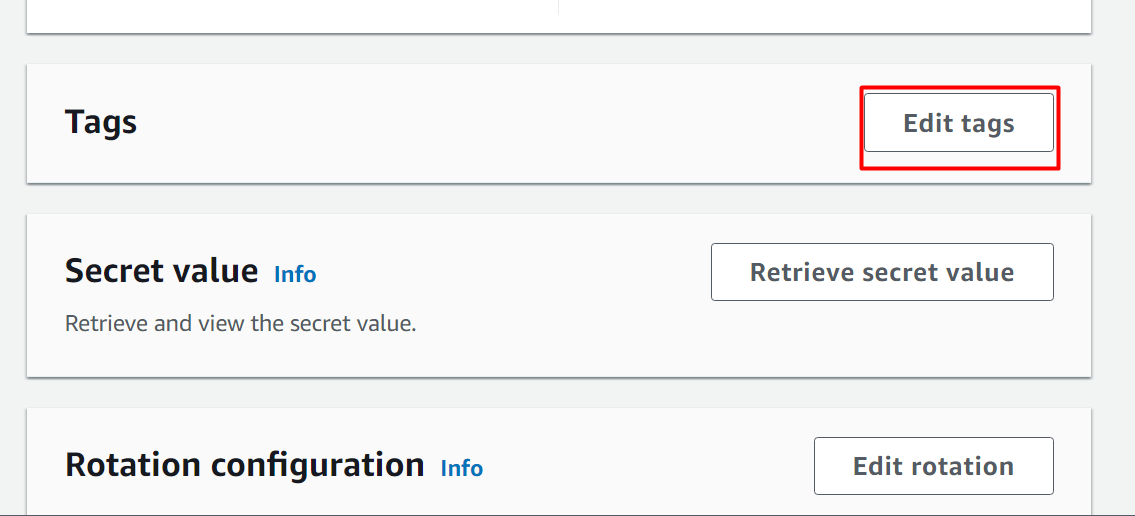
From the following interface, locate the “Tags” section. In this section, tap the “Edit tags” button:
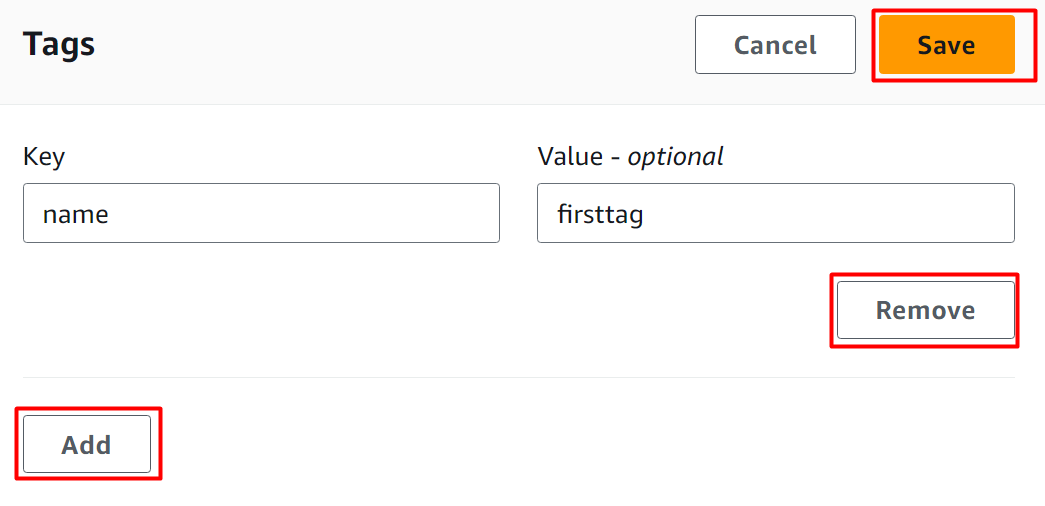
Provide the Key-Value pair for the tags and hit the Save button to apply changes:
- Add: To add multiple tags to a Secret, click the “Add” button.
- Remove: Similarly, to remove any existing tag, tap the “Remove” button.
Method 4: Delete a Secret
Secrets are critical to delete and therefore, the Secret Manager does not immediately delete a secret. Instead, the user will schedule the deletion of the secret. During the scheduled time, the secret will remain inaccessible.
In case of a replicated secret, the user is required to delete the replica secret first and after that, the primary secret shall be deleted.
After creating a secret, choose a secret from the Secret Manager Dashboard:
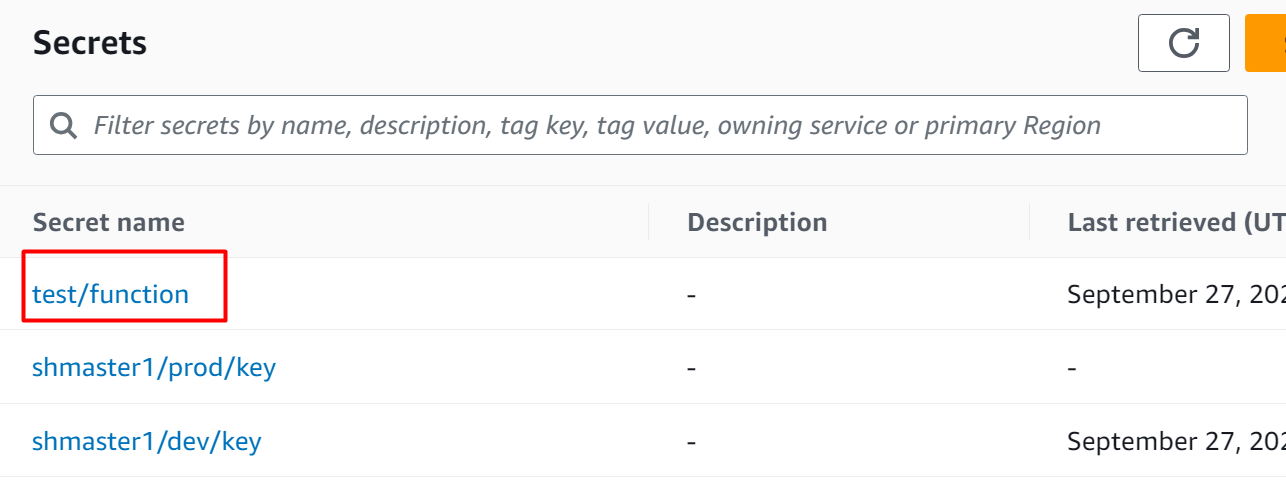
The following interface will be displayed to you. Click on the “Actions” tab from the interface. From the drop-down menu of the “Actions” tab, select the “Delete secret” button:
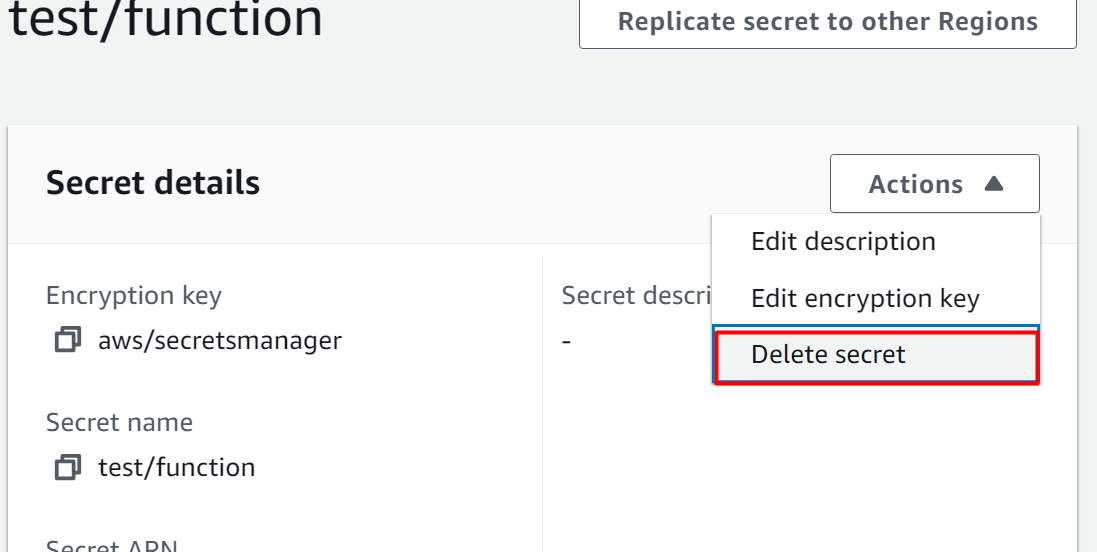
A pop-up window will appear. On this window, the user can schedule the deletion by providing the number of days between 7 to 30 days in the “Waiting period” section. After configuring it, click on the “Schedule deletion” button:
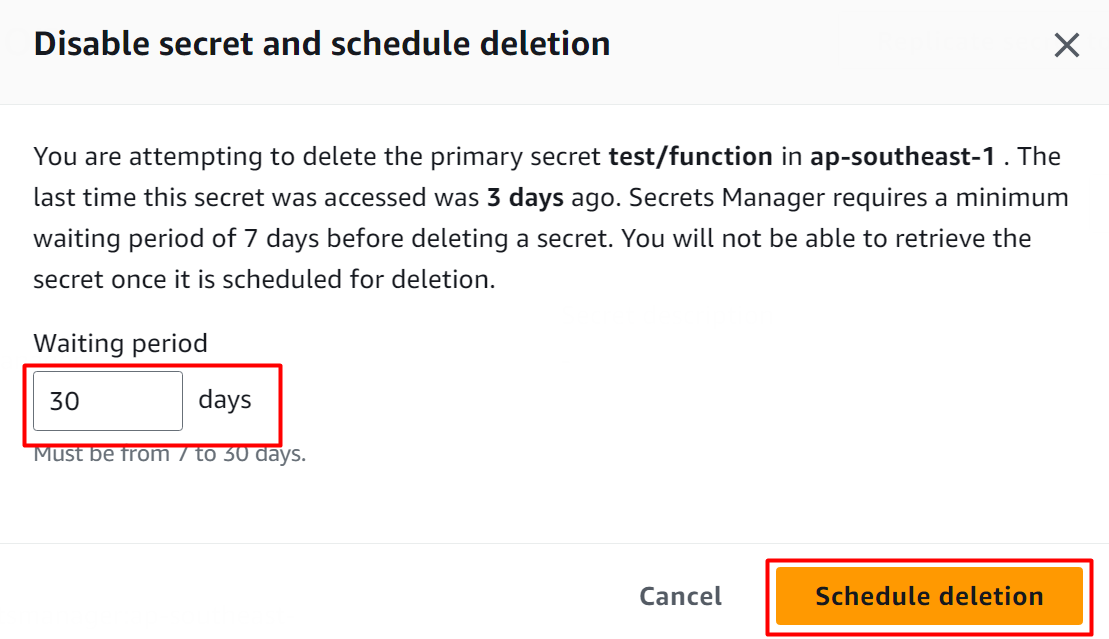
AWS will display a confirmation message upon the successful scheduling of the Secret:
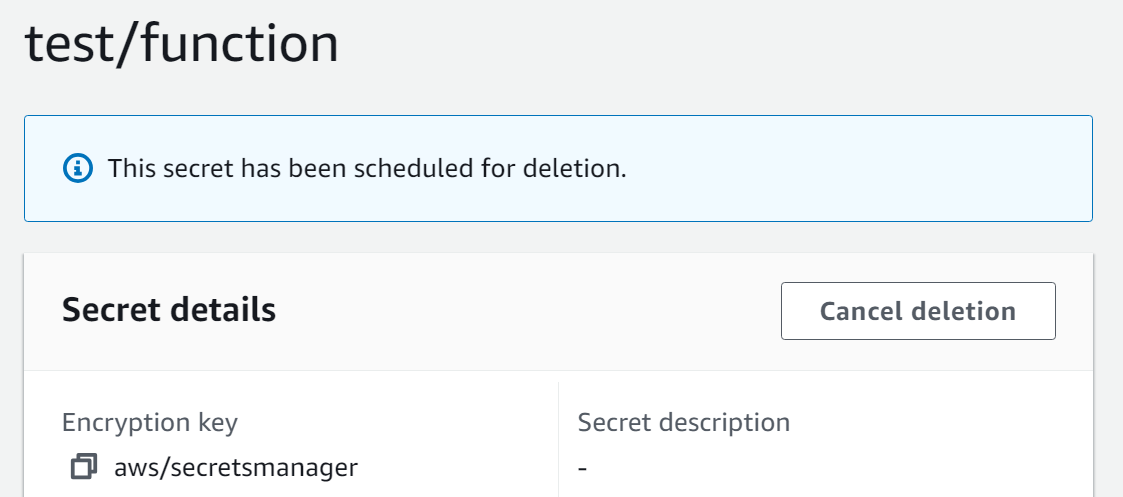
Method 5: Restore a Secret
When a secret is scheduled for deletion, it is marked as a deprecated secret and cannot be accessed directly. This inaccessibility of the secret remains till the recovery window ends. The secret will be permanently deleted once the specified time of recovery window is met.
However, the secrets can be restored by following some simple steps which are mentioned below:
For restoring a secret that was deleted accidentally, the user can follow a few simple steps. To restore a secret, click on the “Preferences” icon located in the top-right corner of the interface:
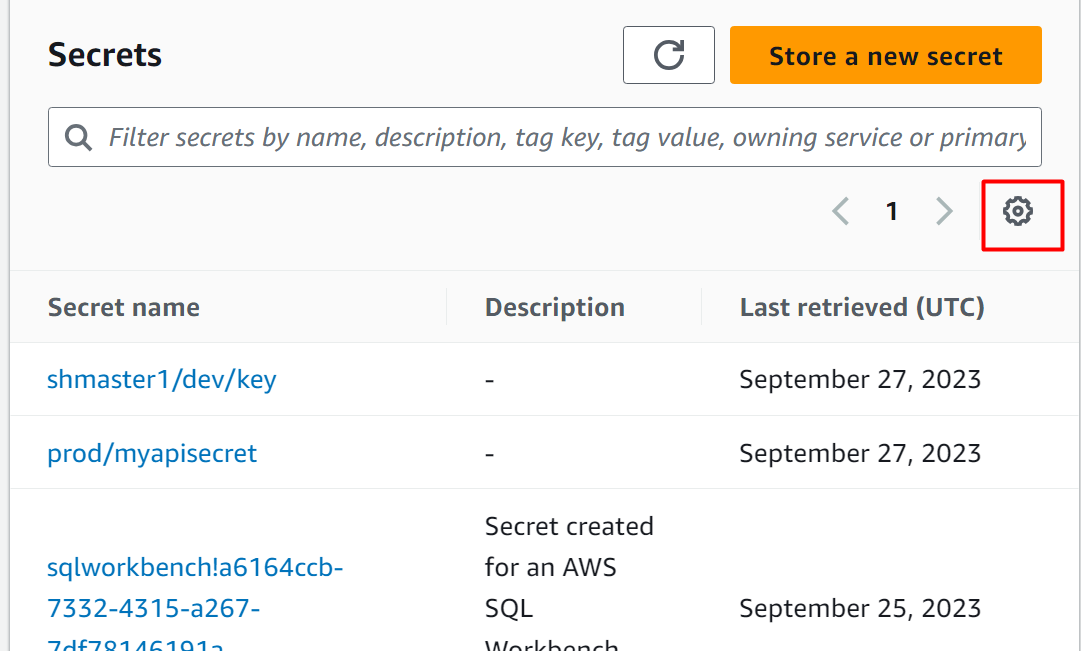
From the pop-up windows displayed, enable the “Show secrets scheduled for deletion” option. Keeping the defaults, click the “Save” button:
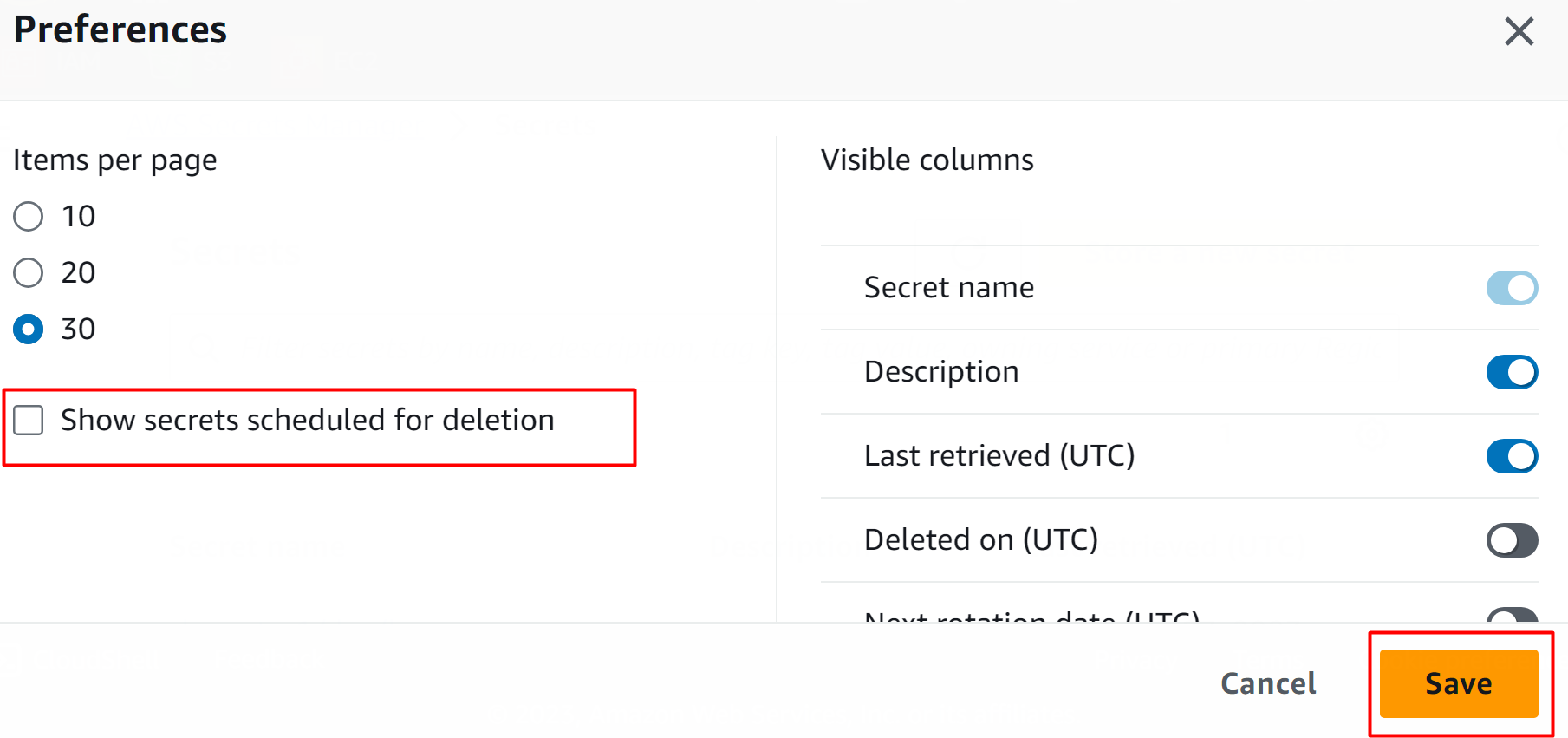
AWS will display a confirmation message. On the dashboard, all the secrets that were scheduled for deletion will be displayed to the user. Note that only those secrets will be displayed that haven’t exceeded their scheduled time of deletion. Click on the secret that you want to restore:
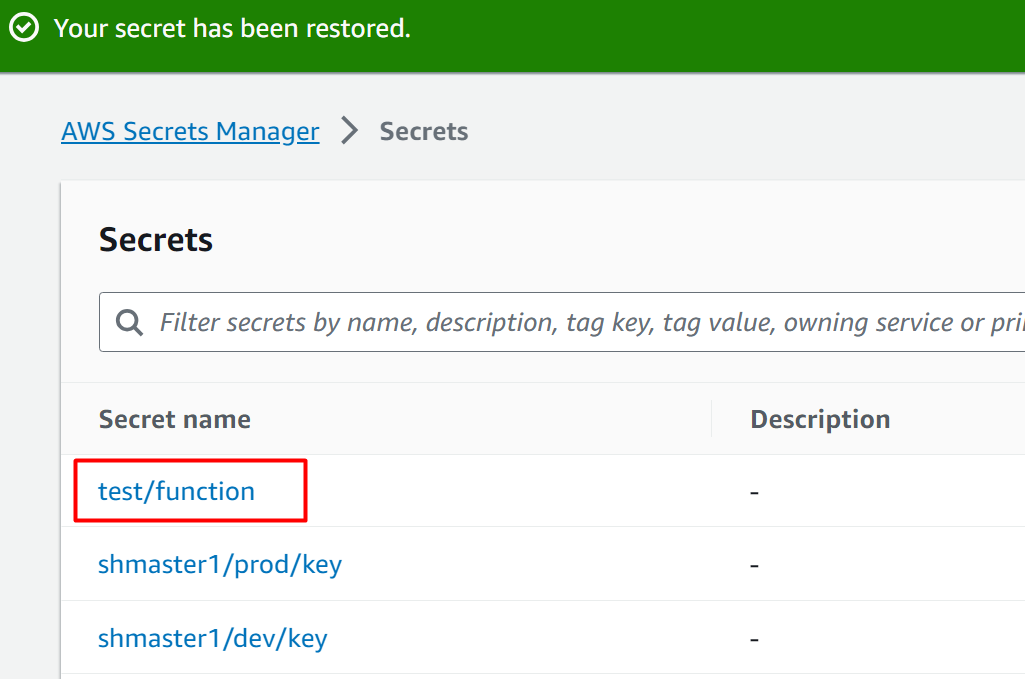
Click on the “Cancel deletion” button to terminate the deleting schedule of the secret:
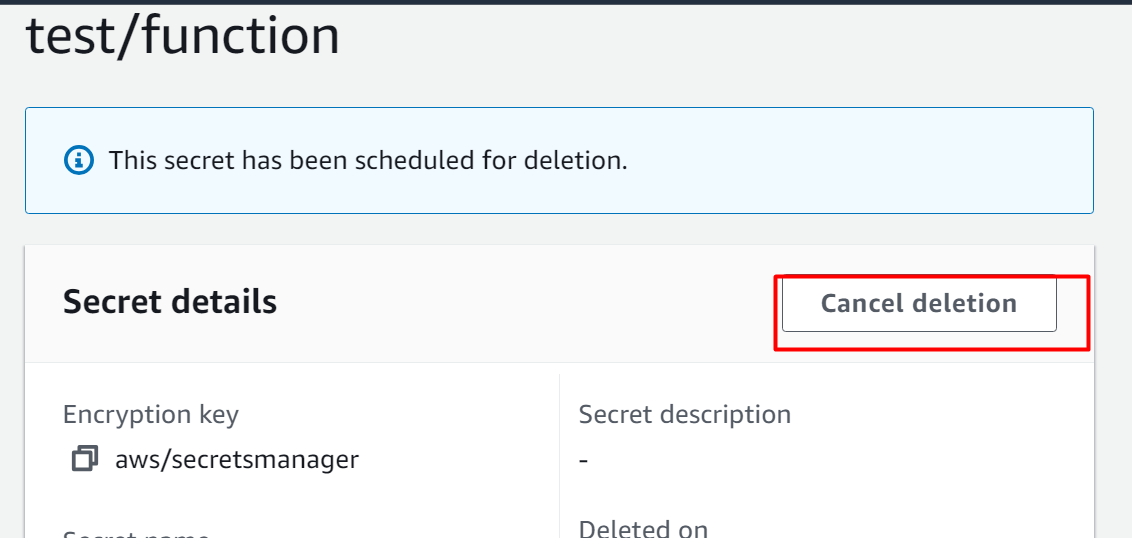
Confirm the deletion by tapping the “Cancel deletion” button:
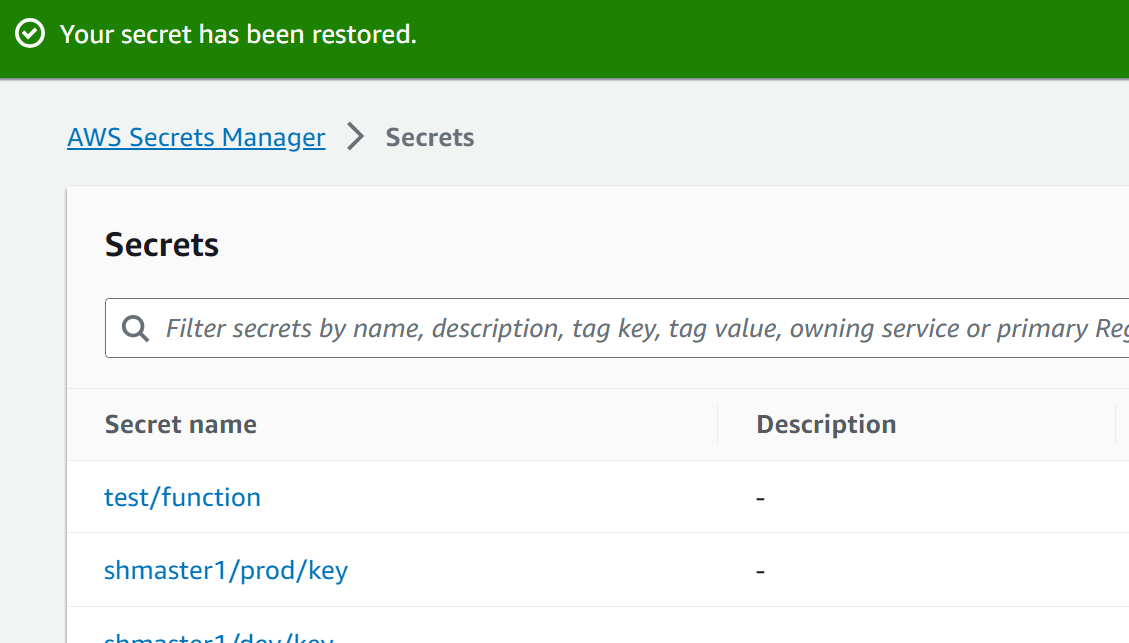
The secret has been restored successfully as indicated by the AWS confirmation message:
Method 6: Change the Description of a Secret
Apart from updating values, changing keys, and deleting and restoring the secret, AWS users can also edit the description of the secret. To change the description of a secret, choose the secret from the AWS Secret Manager Dashboard:
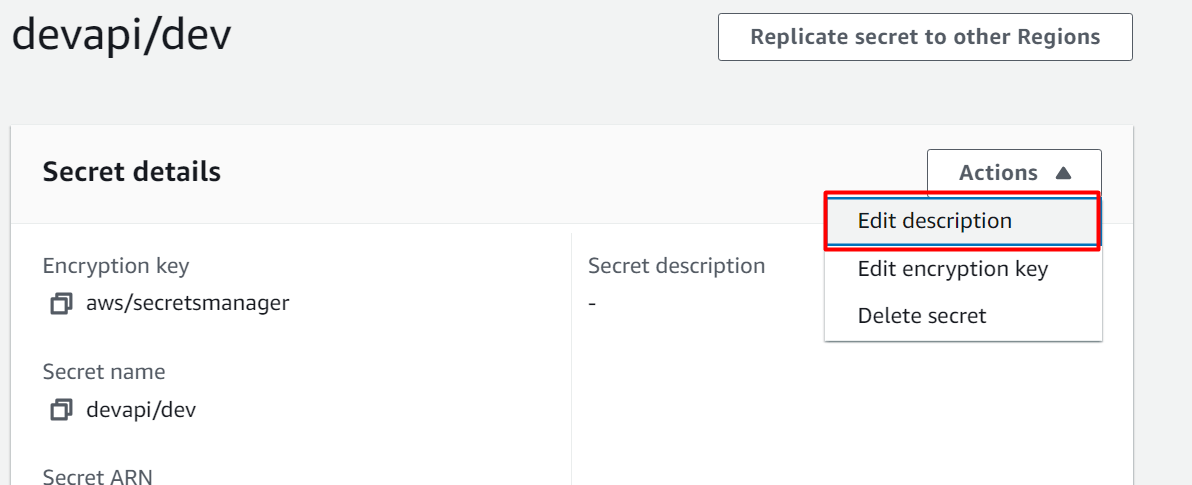
On the next interface, tap the “Actions” button and click on the “Edit description” option from the drop-down list:
This will open the following dialog box. In the Description field, edit the description and hit the Save button to apply changes:
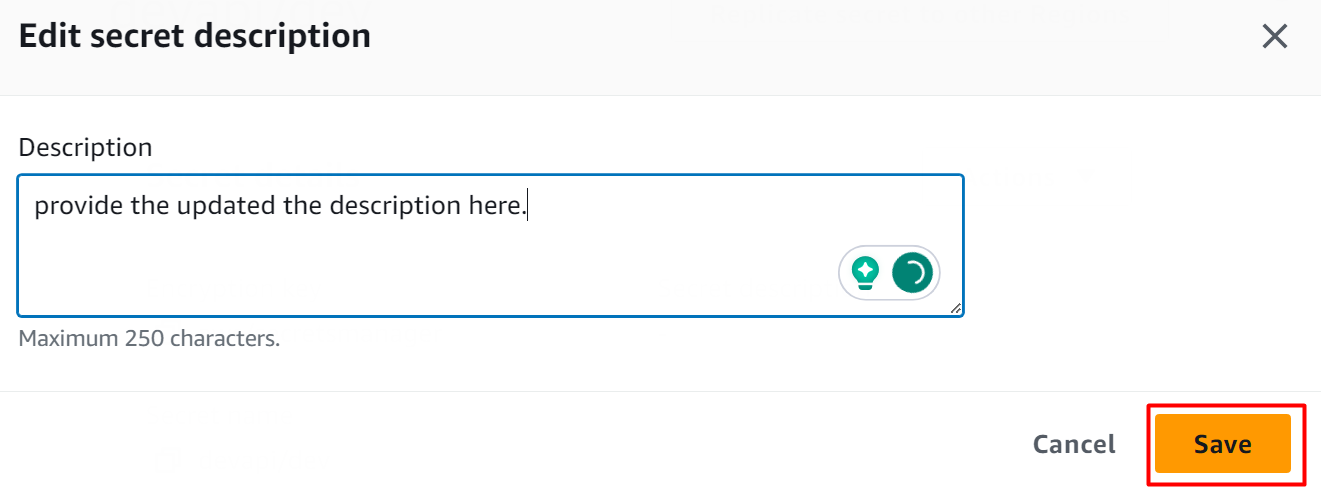
The description has been updated successfully:
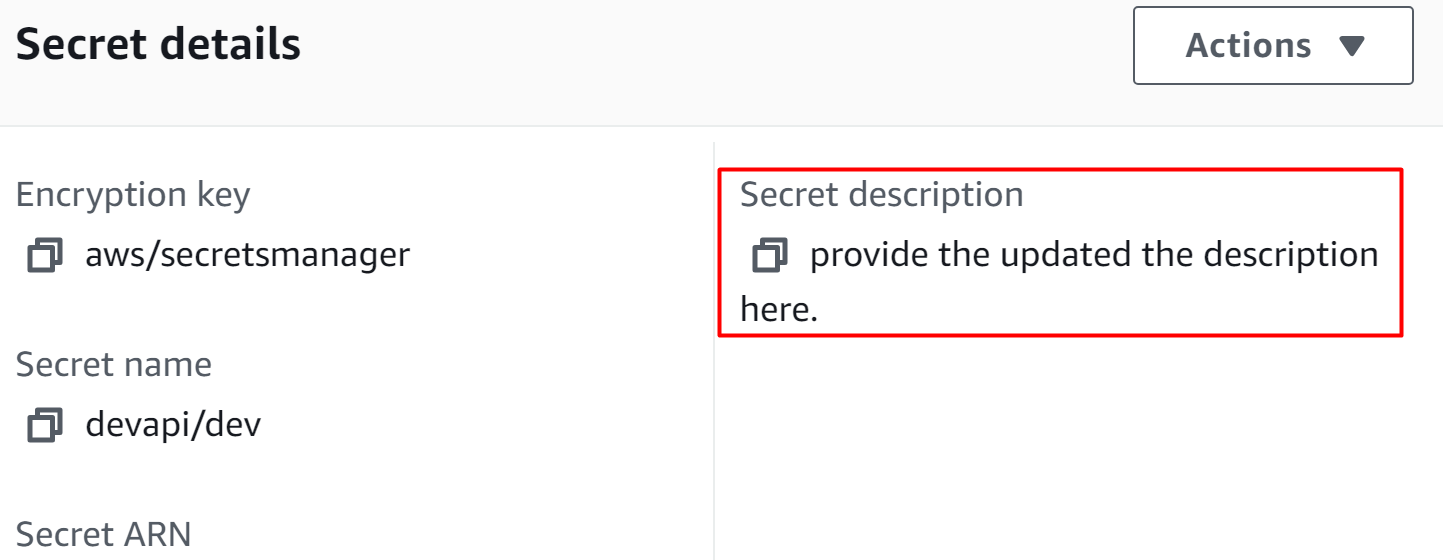
That is all from this guide.
Bonus Tip: Key Features of AWS Secret Manager
While talking about the various actions a user can take with AWS Secret Manager, let’s explore some key features of Secret Manager that make it your go-to service for storing and securing credentials:
Rotate Secrets Safely: This service offers built-in integrations for a vast portfolio of AWS services such as MySQL, PostgreSQL, Lambda functions, Aurora, RDS, etc. A recommended practice is to enable versioning while rotating the secrets in order to prevent the breaking of the application.
Fine-grained Access controls: Multiple methods are provided for securing the credentials such as accessing them by using Tags, implementing hierarchical names for scalability, cross-account access, etc.
Audit and Monitor: Users can encrypt and decrypt secrets by using the encryption key services of AWS and monitor the activity in CloudWatch and CloudTrail etc.
Pay-as-you-go: AWS Secret Manager follows pay-as-you-go models which means that the user is only charged for the features it utilizes.
Conclusion
To modify secrets in the AWS secret manager, the user can change the tags and encryption keys, update the key’s values, and delete and restore the secrets. By using the AWS Secret Manager, the security architecture of the application is improved as hard-coded are get ridden off. These values are then replaced with the runtime accessed value of the secrets through Secret Manager. This article is a step-by-step manual for modifying the secrets in AWS Secret Manager.
Source: linuxhint.com
