How to Find The Cause of Segmentation Fault in C++
Segmentation faults can be challenging to debug because they often result in crashes without providing detailed error messages. However, tools like GDB (GNU Debugger) can help identify the source of the segmentation fault by examining the program’s state and stack trace at the time of the error.
It’s important to note that the segmentation faults are typically caused by programming errors and are considered bugs. They should be fixed by reviewing and correcting the problematic code. Common causes of segmentation faults include:
- Dereferencing the null or uninitialized pointers
- Writing or reading outside the limits of an array
- Using a memory that has previously been deallocated or released
- Stack overflow or stack corruption
- Using uninitialized variables
By carefully examining your code and using debugging tools like GDB, you can identify and fix the segmentation faults, ensuring that your program operates correctly and does not encounter these errors.
GDB Debugger
GDB (GNU Debugger) is a powerful debugging tool that helps to identify and analyze the issues in compiled programs including segmentation faults. It enables you to examine the state of the program, trigger the breakpoints, and observe the execution flow.
To use GDB effectively to debug the segmentation faults, you need to compile your C++ program with the enabled debugging symbols. These symbols include additional information about the program’s structure, variables, and functions which aids in the debugging process.
Finding the Segmentation Fault in C++ with GDB
Here’s an example code snippet that causes a segmentation fault:
int main() {
int* ptr = nullptr;
*ptr = 5;
return 0;
}
Let’s first explain the code. Then, we will discuss in steps about finding a segmentation fault in the previous code.
The “#include <iostream>” preprocessor directive adds the required <iostream> header file which offers the input as well as the output stream characteristics in C++.
Inside the main() function, there is a declaration of a pointer variable “ptr” of type int*.The “nullptr” value is used as the pointer’s initialization which is a special null pointer value that indicates that it does not point to any valid memory location.
Dereference attempts are made with the null pointer “ptr” in the following line which is “*ptr = 5;”. In this case, since “ptr” is set to “nullptr”, there is no valid memory location to access.
Now, we will discuss some steps that need to be adopted to compile the program in order to find the segmentation fault.
Step 1: Enable the Debugging Symbols
To start, make sure to compile your C++ program with the enabled debugging symbols. To provide the debugging information to the executable file during compilation, use the “-g” flag. Consider the case where we have a C++ file called “main.cpp”.
Step 2: Run GDB
Once the program is compiled with debugging symbols, run GDB by passing the executable file as an argument.
Step 3: Start the Program
Start the program by typing “run” or “r” at the GDB prompt:
Your program will then begin to execute.
Step 4: Identify the Segmentation Fault
The program continues to run until it encounters a segmentation fault. The program then stops running, and GDB produces an error message.
For example: let’s consider the previously-explained code where when we try to assign the value of 5 to the memory location that is pointed to by the null pointer, it results in a segmentation fault. The program immediately terminates at the line where the segmentation fault occurs.
When running this program with GDB, you will see a similar output to the following:
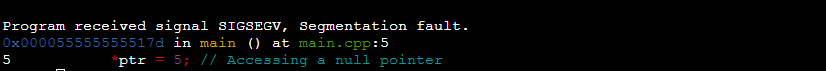
This output indicates that a segmentation fault occurred in the main function at line 5 of the “main.cpp” file.
Step 5: Examine the Stack Trace
To gain more insights into the segmentation fault, you can examine the stack trace using the “backtrace” command or simply “bt”. This command displays the sequence of function calls that leads to the crash.
The stack trace is displayed which indicates the functions that are called before the segmentation fault:
![]()
This output tells us that the segmentation fault occurred in the main function at line 5 of the “main.cpp” file.
Step 6: Set the Breakpoints
To investigate further, you can set the breakpoints at specific lines of code to halt the program’s execution at those points. This allows you to inspect the program’s state and variables. For example, to set a breakpoint at line 5 of the “main.cpp”, use the “break” command as follows:
This sets a breakpoint at line 5 of the “main.cpp” file:
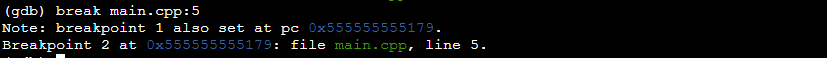
Step 7: Resume the Execution
After setting the breakpoints, resume the program’s execution using the “continue” command or simply “c”:
The program continues running until it reaches the breakpoint.
Step 8: Inspect the Variables and Code
Once the program halts at a breakpoint, you can use various GDB commands to examine the variables, step through the code, and investigate the cause of the segmentation fault.
Step 9: Quit GDB
Once you finish the debugging, you can exit GDB using the “quit” command:
This provides a basic overview of using GDB to find the segmentation faults in the C++ programs. GDB provides many more features and commands that can help with debugging, and you can refer to the GDB documentation for a more in-depth information.
Conclusion
This article demonstrates the utilization of GDB to find the segmentation fault in C++. We explained to you the steps that need to be followed. These steps provide a comprehensive explanation on how to find a segmentation fault in C++ using GDB. By following these steps and utilizing GDB’s features, you can effectively locate and debug the source of the segmentation fault in your C++ program.
Source: linuxhint.com
