Free XSS Tools
After reading this tutorial you will know how to install and get started with the most popular free tools to find and exploit Cross-site scripting security holes.
Some of the tools included in this tutorial are already included in Kali Linux and other security-oriented Linux distributions. Yet this tutorial also explains the installation process for all of them.
The PwnXSS Vulnerability Scanner
PwnXSS is a XSS vulnerability scanner which includes functions like links crawling, POST and GET forms, error handling, supports multiprocessing, cookies and customization settings.
Before downloading PwnXSS, install bs4 using pip as shown below.
Also install requests by executing the command shown in the screenshot below.
Get PwnXSS as shown in the following figure:
Give proper permissions using the chmod command.
Enter the PwnXSS directory.
Launch PwnXSS with Python as shown below, followed by the -u flag, and the URL you want to scan. In the example below, <URL> must be replaced with your target, including the proper protocol (http or https).
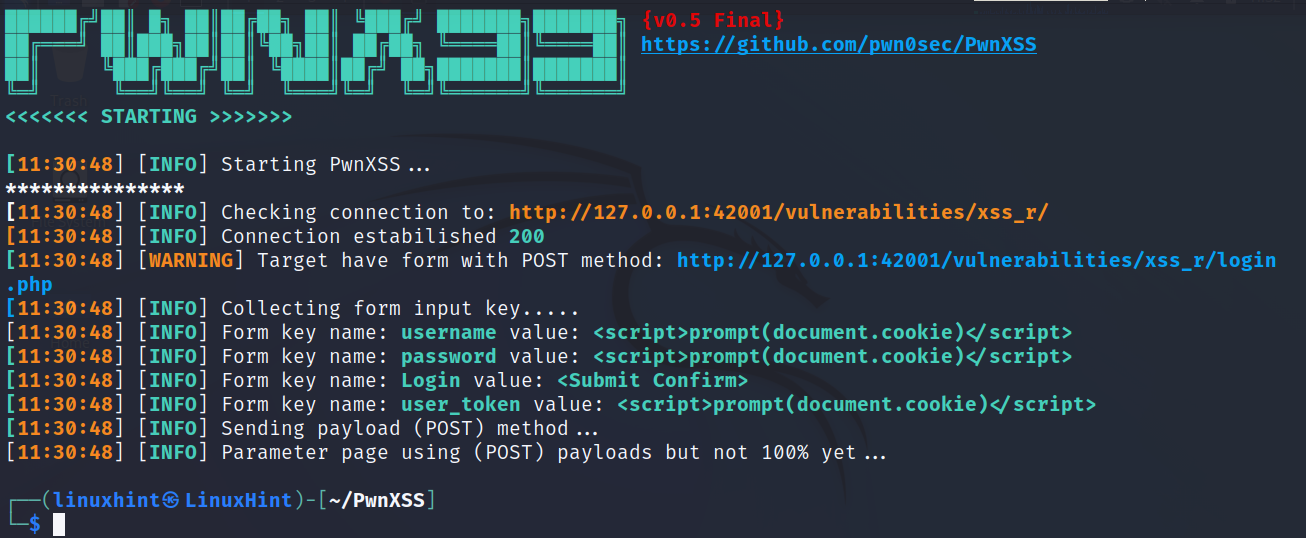
Wait for the results.
Scanning XSS Vulnerabilities With XSStrike
This is another Cross Site Scripting (XSS) vulnerability detection tool with a payload generator, fuzzing, and crawler.
XSStrike works differently than other XSS scanners. It analyses replies with different parsers and then crafts payloads according to the context analysis integrated with a fuzzing engine.
XSStrike Features
- Reflected and DOM XSS scanning
- Fast crawling
- Context research
- Configurable core
- WAF detection and evasion
- Outdated JS lib scanning
- Smart payload generator
- Handmade HTML & JavaScript parser
- Fuzzing engine
- Blind XSS support
- Tested work-flow
- Full HTTP support
- Bruteforce payloads
- Payload Encoding
Use git to download XSStrike as shown below.
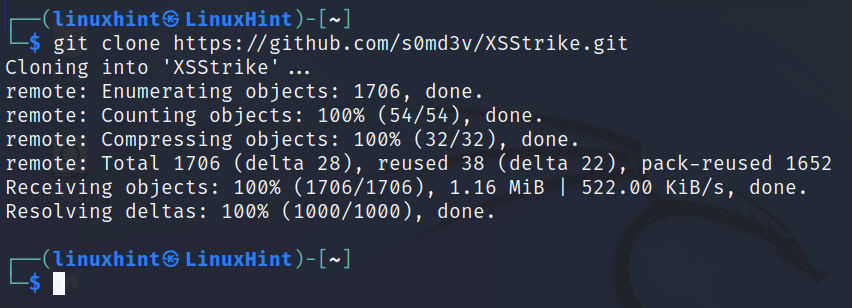
Go inside the XSStrike directory.
Run the following command to install necessary dependencies:
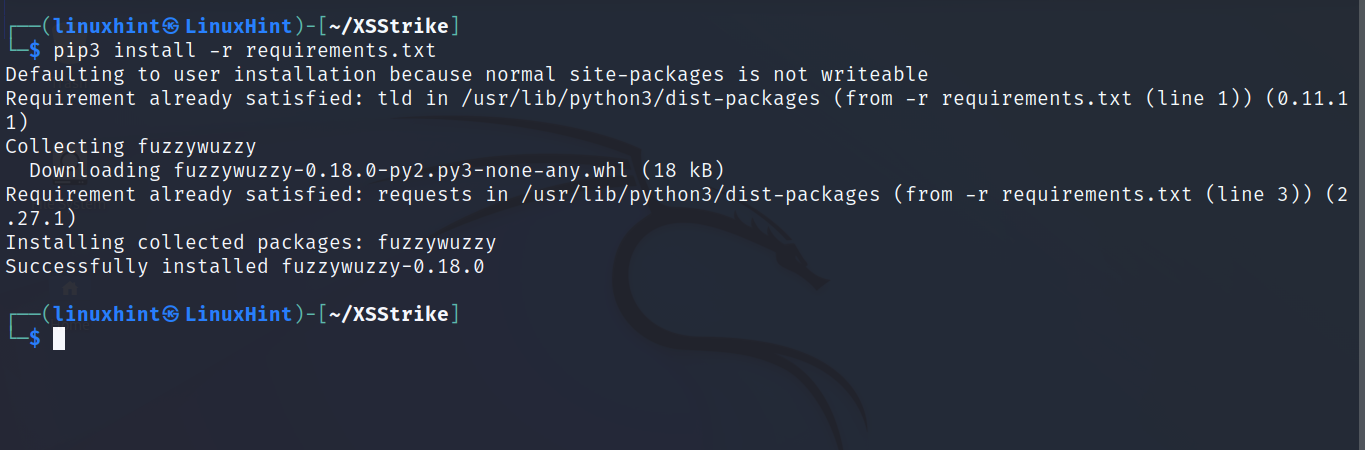
After installing dependencies, you can run XSStrike as shown below. In this example I’m using the crawling feature. Replace <URL> with the actual URL you want to scan.
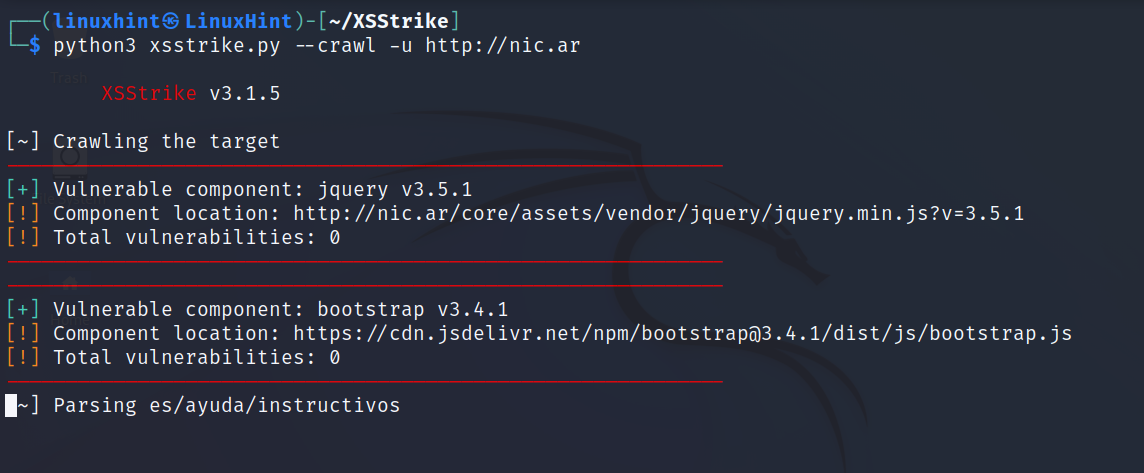
As you can see in the previous screenshot, XSStrike will return a list of vulnerabilities if found.
Scanning and Exploiting XSS Security Holes With xsser
The Cross Site “Scripter” ( XSSer) utility is an automatic framework to find and exploit XSS security holes. It includes both text and graphical modes.
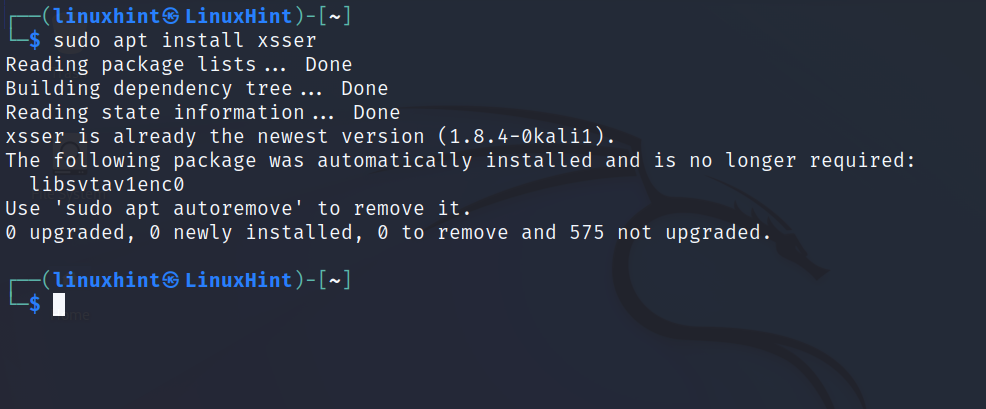
If you are using Kali Linux, you can install xsser from repositories using apt as shown in the image below; otherwise keep reading below.
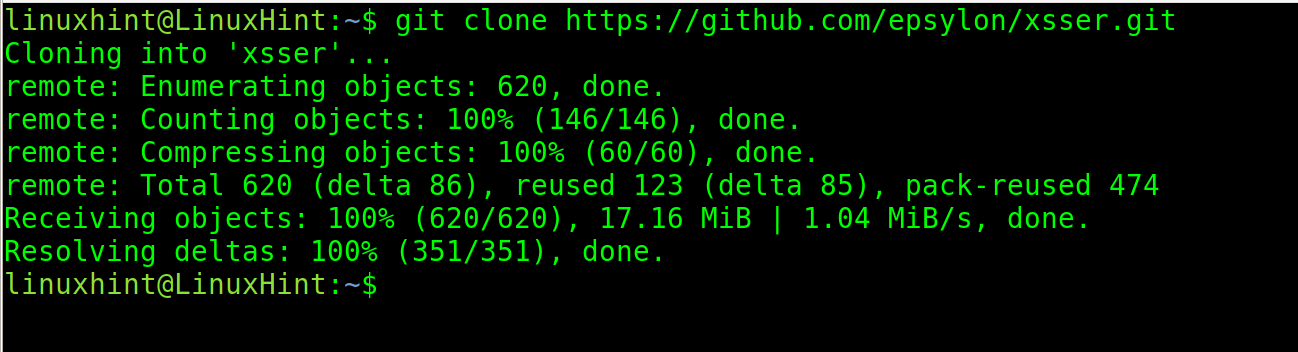
If you are using a different Linux distribution, use git to download xsser.
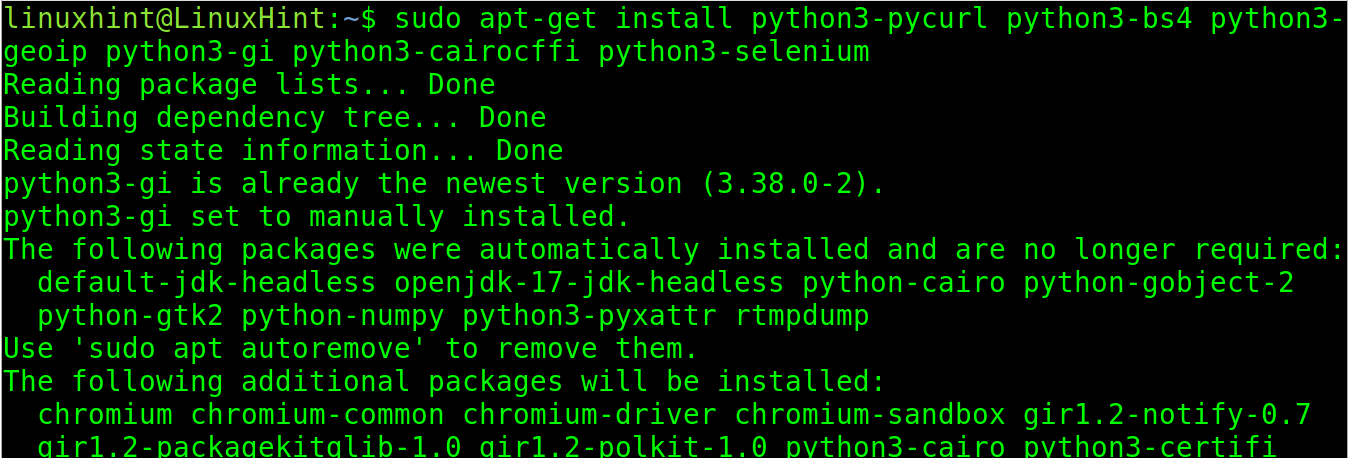
Install the following dependencies:
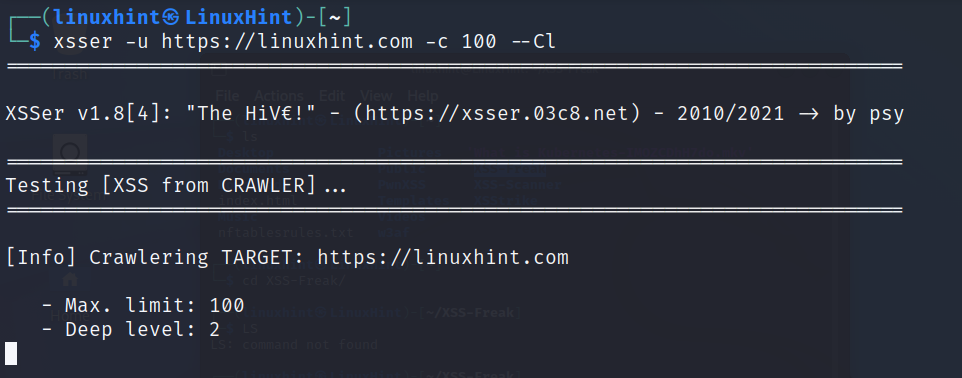
To use xsser in the Linux console, use the following syntax. In the example below, I use the crawling feature. You can execute xsser without flags to see all available options.
This tool also includes a GUI for users who are not familiar with the Linux terminal.
To launch the graphical mode run:
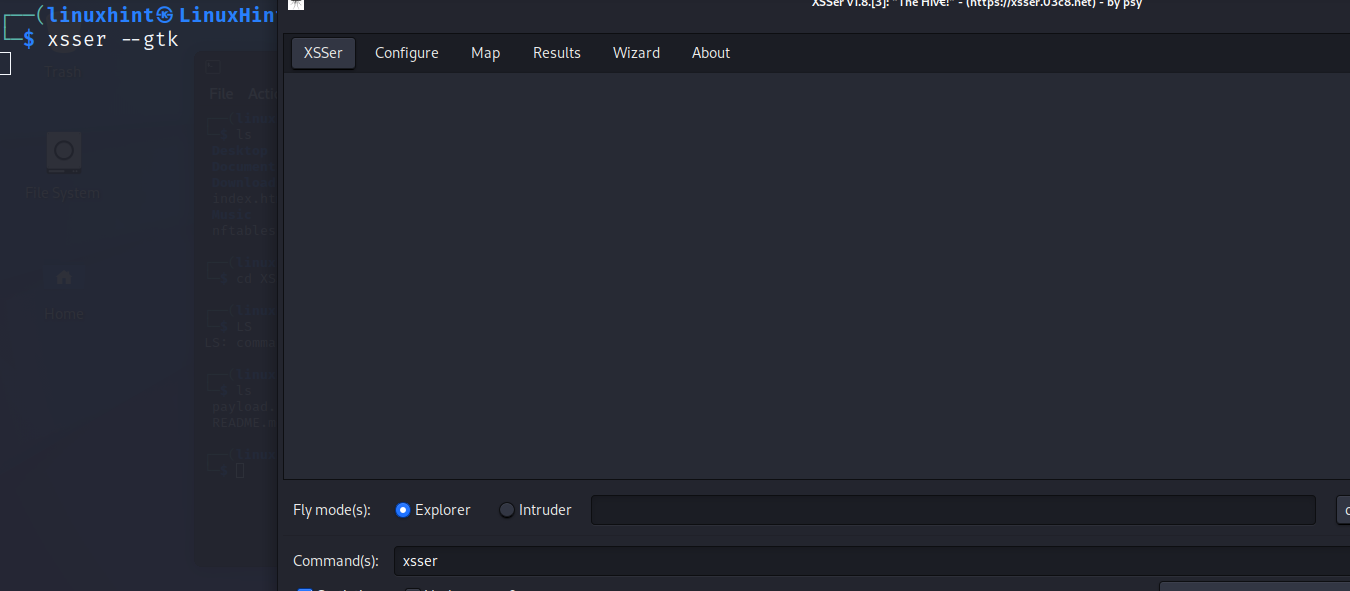
Xsser GUI is very intuitive, if you don’t feel comfortable with the Linux console, try it.
OWASP ZAP (Zed Attack Proxy)
OWASP ZAP is an awarded graphical security scanner which can be used for Cross-site request forgery attacks and to detect XSS vulnerabilities.
To install it on Debian based Linux distributions run the following apt command:
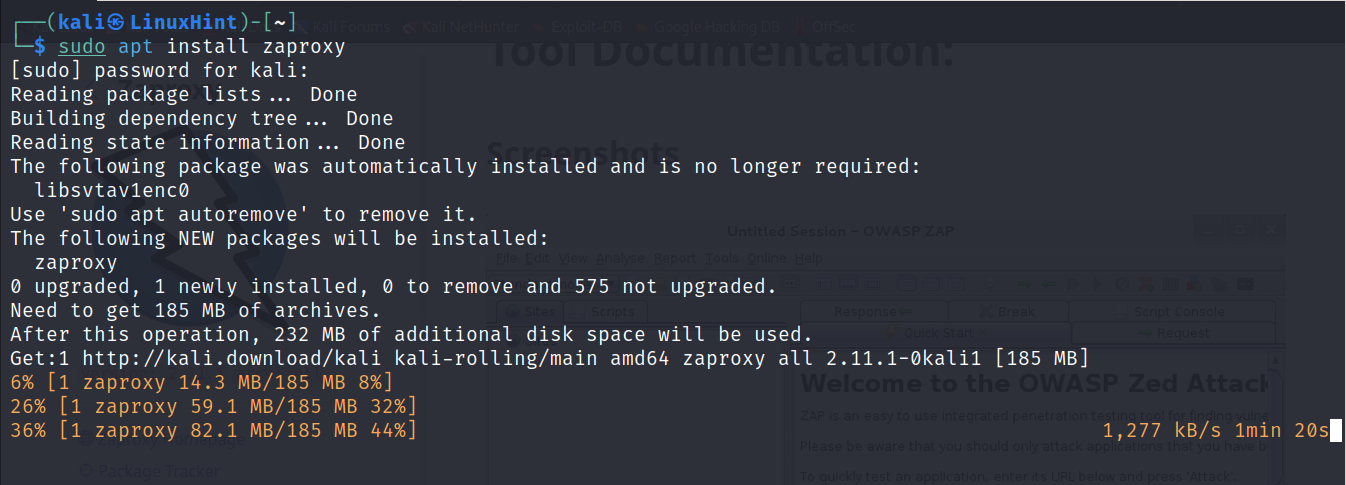
To run it execute:
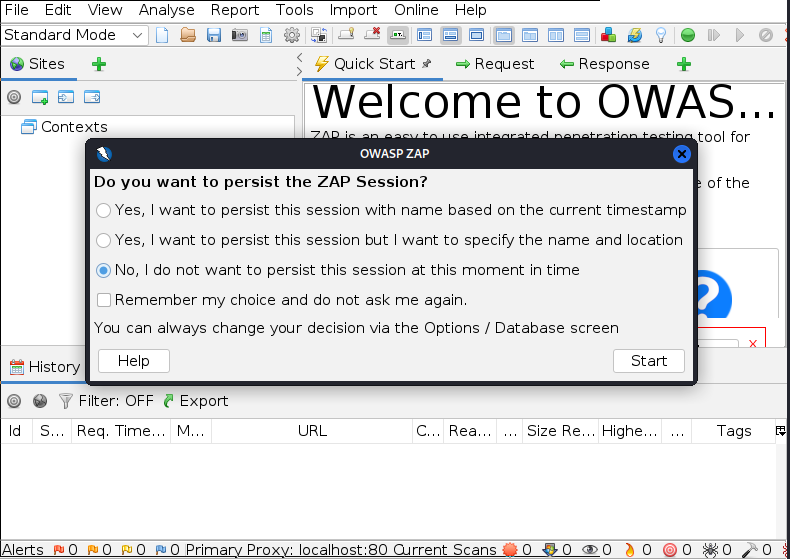
Choose the best option for you, you can choose for a persistent session or a unique one, then press the Start button.
After starting ZAP, you will be offered to install Add-ons.
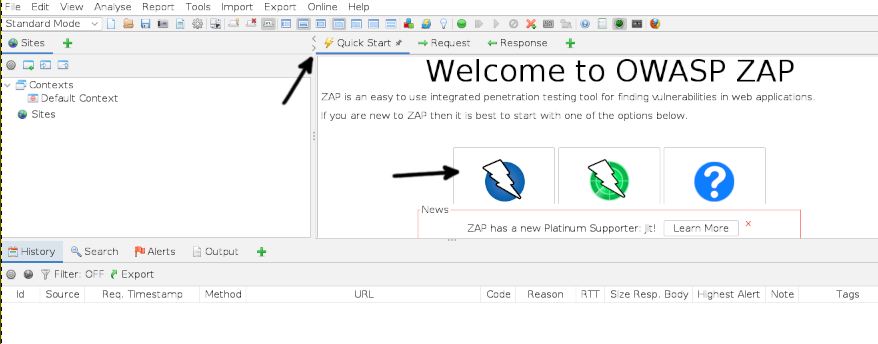
To quickly launch a ZAP scan, press the Quick Start button and then press the automatic scan button as shown below.
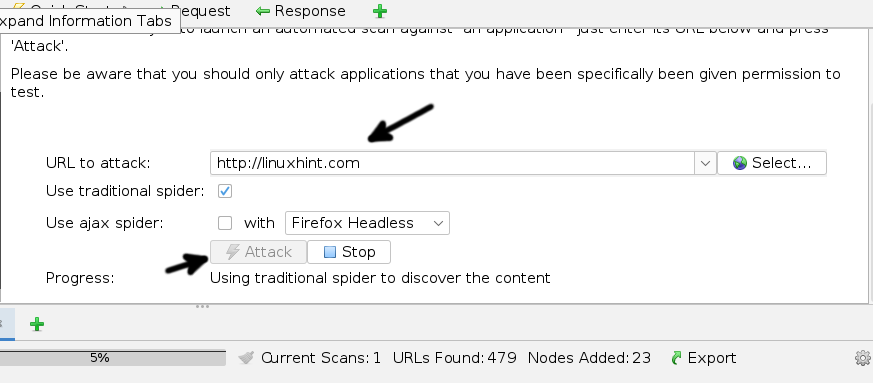
Fill the URL to scan and press the Attack button.
This is one of the best vulnerability scanners, probably the most recommended one in this article.
The Free XSS-Freak Tool
The XSS-Freak vulnerability scan crawls websites looking for all links and directories and then executes XSS payloads.
Note that in my case, this scanner produced errors when executed. It requires a minimum edition of its code explained below.
To get it use the git command as shown below.
Enter the XSS-Freak directory.
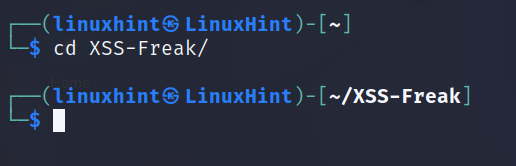
Try to run it, you can use the –help flag.
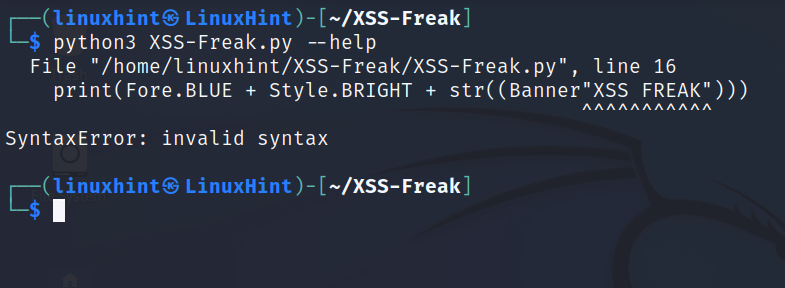
If, when trying to run it, produces the error shown in the above screenshot, open the XSS-Freak.py file with a text editor.
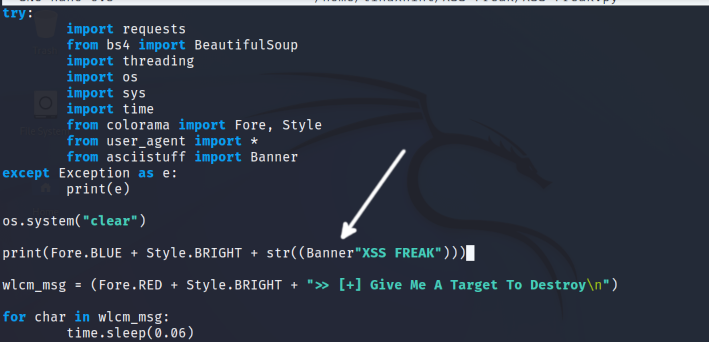
Remove “Banner”, changing the previous screenshot as shown below.
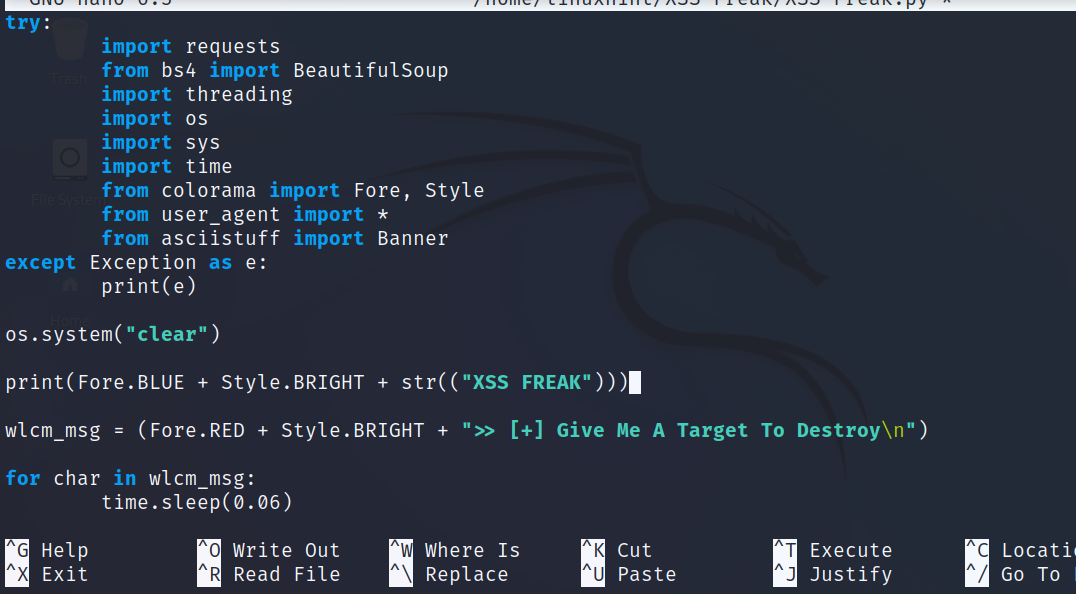
Get a payloads list. You can use the following command to get a payloads list file:
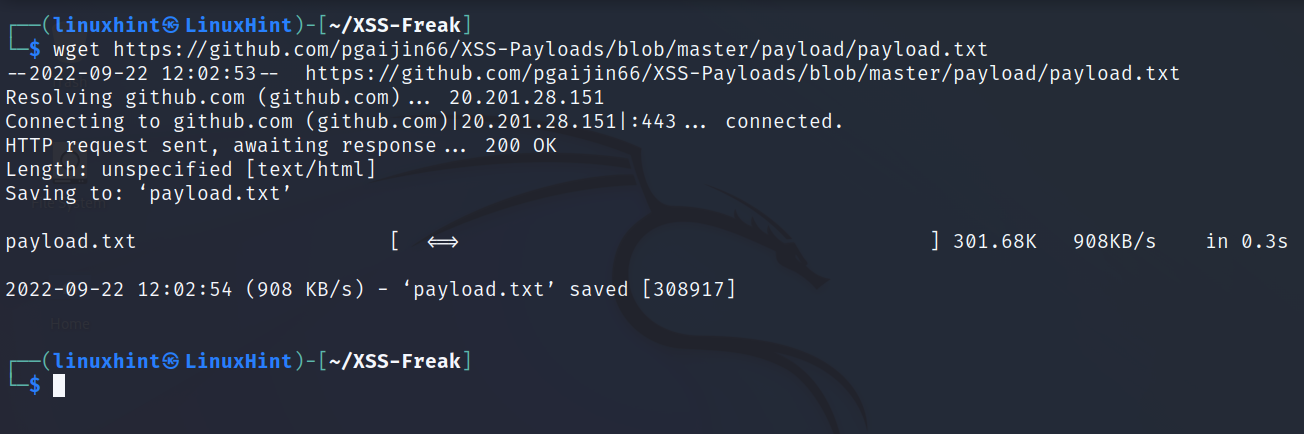
Now, run XSS-Freak and fill the required information.
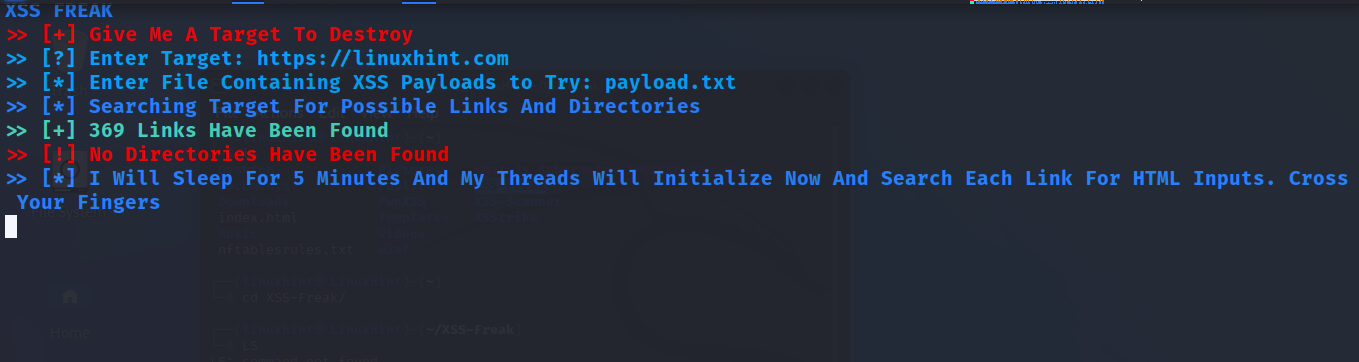
As you can see, this is a command line interactive scan.
The BurpSuite
BurpSuite is probably the most used tool for XSS vulnerability detection and exploitation.
It is included in Kali Linux by default and available in repositories of almost every Linux distribution.
On Debian based distributions like Ubuntu, you can install BurpSuite using the apt packages manager as shown below.
Then, open it from the Linux console or the Applications menu.
BurpSuite will ask you if you want to start a temporary project, to open a ready project, or start a new persistent one. Choose the best option for you and press the Next button.
Select Burp defaults and press Start Burp.
Confirm the interception is turned on by pressing the Proxy tab.
Then, start browsing the page and press the Dashboard tab.
XSS-Scanner
The XSS-Scanner identifies vulnerable URLs, forms and headers and tests vulnerabilities by injecting code.
To get it, use the git command as shown below.
Enter into the directory.
Run the following command. If npm is not installed, the process will ask you if you want it to be automatically installed; otherwise run sudo apt install npm.
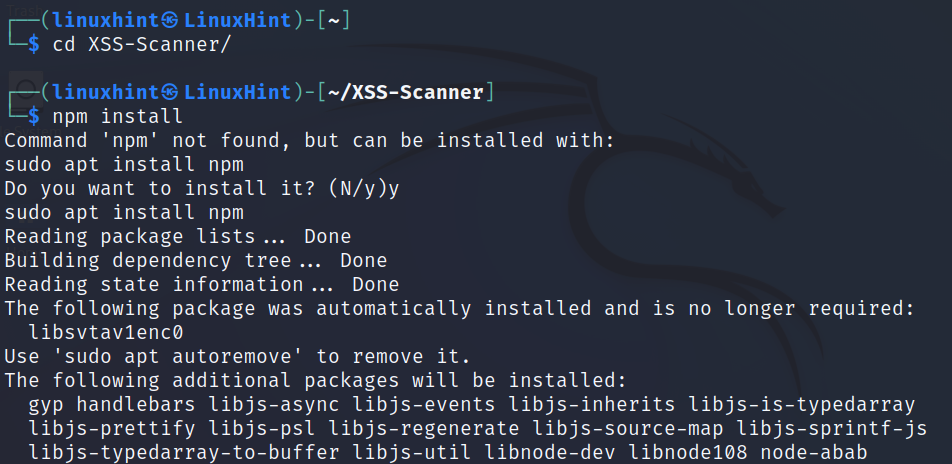
Install nodemon by executing the following command:

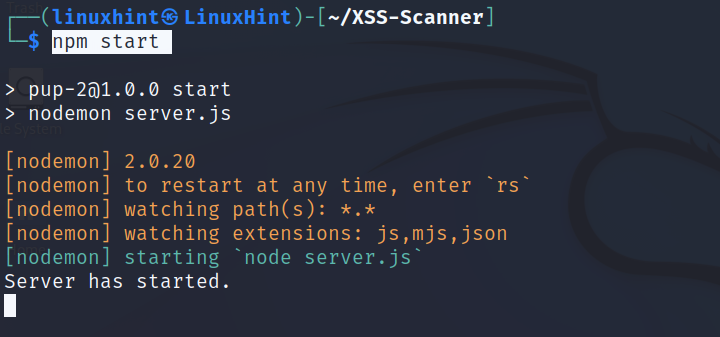
Start npm by executing the command shown in the image below.
Access the URL http://localhost:4000/ and start scanning your target.
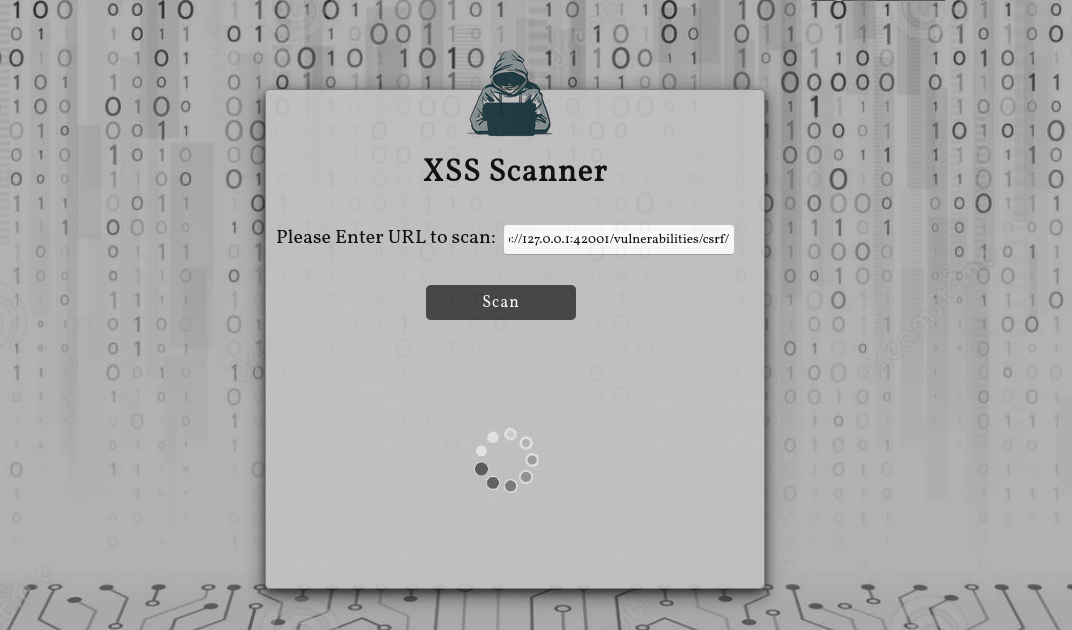
Wait for the results to show up.
Conclusion
There are many XSS free tools in the market, especially for Linux. Users can choose both graphical or text mode utilities. Installing and launching these programs is pretty easy. Yet, exploiting the vulnerabilities may require a little more of knowledge. To test these tools, I highly recommend the DVWA insecure environment for testing. This web application already includes security holes for researchers to try pen testing resources. Since most tools are installed using Python, the instructions in this document are valid for almost every Linux distribution. The scenarios used in the examples are Kali and Debian.
This article was initially written in 2020 and updated in 2022, removing discontinued tools and adding current ones.
Thank you for reading this tutorial describing the most popular free XSS scanning and exploiting tools. Keep following our blog for additional IT security content.
Source: linuxhint.com
