Basic Linux PAM Modules
Like any typical authentication protocol, using PAM relies on understanding an array of concepts. The PAM components you should internalize and master include the control groups and control flags.
Notably, Linux PAM has four management groups that every user should know. They include:
- Auth Group – They help in validating the users. They verify the username, password, and other authentication details.
- Account Group – They control the access to a service or program such as the number of times you should access or use a service. They also control the other conditions such as account expiration and time.
- Session Group – This group takes the responsibility for the service environment, particularly in starting and ending a session.
- Password Group – This group come in handy when updating the passwords.
For control flags, you will find the requisite, required, sufficient, and optional control flags. As the name suggests, control flags control the access to programs based on the behavior of each control flag type.
Apart from the two components, another significant PAM component that you should consider are the PAM modules—and this is what this article will handle. This article will define the various PAM modules and will provide viable illustrations or examples.
But before we look into the modules, let us look into the order of PAM modules.
Modules Order
The order of PAM modules is vital as each module depends on the previous role on the stack. So, a configuration like in the following screenshot will easily allow you to log in:

However, the order in the following screenshot is incorrect and will not allow you an access:

Top 10 Basic PAM Modules
The following PAM inbuilt modules exist in your systems, and you should be conversant with each of them for the proper use of Linux PAM:
1. pam_succeed_if module
This module controls the access to users and groups. For example, you can validate the user accounts using this command:
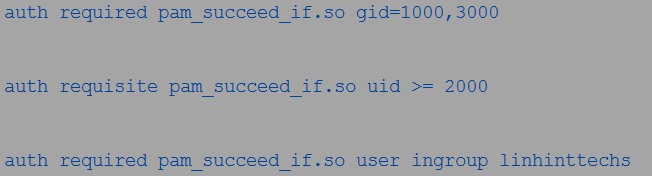
The previous example signifies that only the users whose IDs are 1000 or 3000 can log in.
Another example is as in the following command:
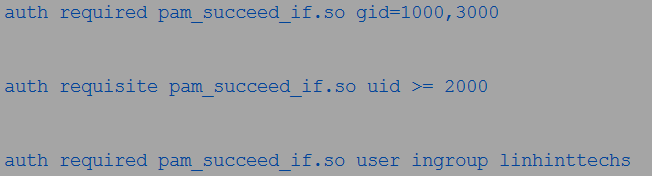
The previous example specifies that only the users with the user IDs equal to or greater than 2000 can access the service or program.
An example of using an ingroup parameter is as seen in the following:
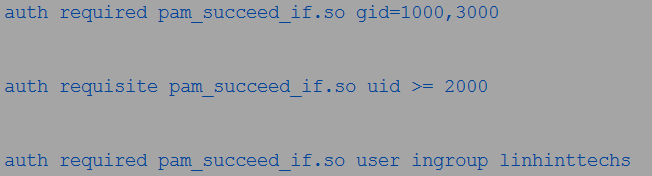
2. pam_deny module
The pam_deny module is commonly used for denying or restricting an access. When used, the module will return a non-OK result upon processing. Using this module at the end of your module stack protects any possible misconfiguration. However, using it at the beginning of a module stack will disable your service, as seen in the following figure:

Interestingly, you can use this module with the account, auth, password, and session management groups.
3. pam_access module
The pam_access module is another module that you can use with all the management groups. It functions the same way as the pam_succeed_if module. However, the pam_succeed_if module does not check the login details from the networked hosts, while the pam_access module focuses on that.
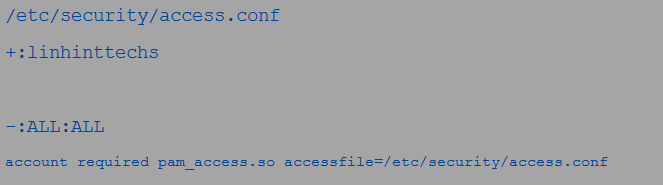
You can then type the access rules as seen in the following figures:
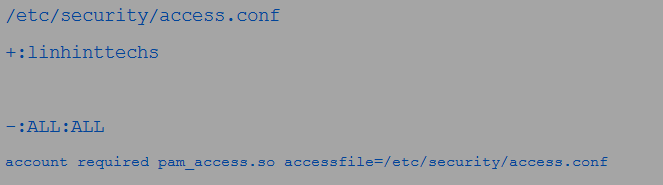
And
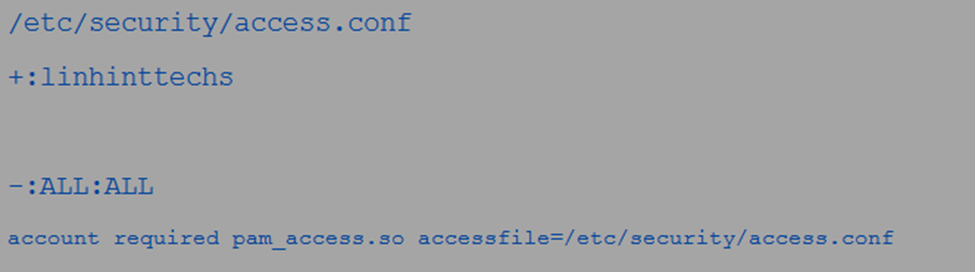
The rules state that only the users within linhinttecks can log in. The + and – signs in the rule allow and deny, respectively. This module is also useable with all the management groups.
4. pam_nologin module
This module is selective and only allows the root to log in should the file exist. Unlike in the previous modules, which you can use with all the management groups, this module is only useable with auth and account management groups.


5. pam_cracklib module
Cybercrime is on the rise, and strong passwords are mandatory. This module sets the rules for how strong your passwords can get. In the following example, the module provides you up to 4 chances to pick a strong password failure to which it will exit. Again, the module provides that you can only pick a password of 12 or more characters.
![]()
6. pam_localuser module
This module is often used to check if a user is in the /etc/passwd. You can use this module with all the management groups including auth, password, session, and account.
![]()
7. pam_rootok module
Only the root users can run this service since it checks if the UID is 0. Thus, this module comes in handy when a service is dedicated to the root users only. It is useable with no other management group except the auth management group.
![]()
8. pam_mysql module
You can use the pam_mysql module to validate the users rather than checking their credentials against the /etc/shadow. It is useable to validate the users with the pam_mysql parameters. You can install it using the following command if you do not have it in your system. This is another module that you can use with all the management groups:
![]()
9. pam_limits module
If you need to set the limits on your system resources, the pam_limits module is what you need. This module affects everyone, including the root users using the limits configuration file available in the /etc/security/limits.d/ directory. It is beneficial in protecting the system resources and is only useable in the session management group.
![]()
The limits set in the /etc/security/limits.conf file can either be hard or soft. Only the root users can change the limit value in hard limits, while the ordinary users cannot. On the other hand, even ordinary users can also change the limit value.
Again, limits can be classified as cpu, fsize, data, nproc, and many more. A good example is shown in the following figure:

The first limit for the linhintadmins members sets the number of processes for each member at 30. On the other hand, the second limit is for the linhintechs members and sets the CPU duration for them at 4000 minutes.
10. pam_rhosts module
It performs the standard network authentication for services and programs often traditionally implemented in rsh and rlogin, among others. The three available options include debug, superuser, and silent. It is only useable with the auth management group and features in the following example:

Conclusion
That brings us to the end of this article. Hopefully, the ten basic Linux PAM modules will prove to be useful in your journey to learn and use PAM.
Sources:
- https://www.oreilly.com/library/view/linux-server-hacks/0596100825/ch01.html
- https://eng.libretexts.org/Bookshelves/Computer_Science/Operating_Systems/Linux_-_The_Penguin_Marches_On_(McClanahan)/12%3A_Linux_Systems_Security/2.06%3A_Pluggable_Authentication_Modules
- http://www.linux-pam.org/Linux-PAM-html/sag-pam_rhosts.html
- https://documentation.suse.com/sles/12-SP4/html/SLES-all/cha-pam.html
- https://www.redhat.com/sysadmin/pluggable-authentication-modules-pam
- https://www.linuxtopia.org/online_books/linux_administrators_security_guide/07_Linux_User_Authentication.html
- http://www.linuxgeek.net/documentation/authentication.phtml
- https://docs.oracle.com/cd/E19683-01/816-4883/pam-32/index.html#:~:text=The%20PAM%20configuration%20file%2C%20%2Fetc,for%20each%20system%20entry%20application.
Source: linuxhint.com
