A Comprehensive Guide on AWS Security Credentials
This article will explain the AWS security credentials and provide best practices to follow for better security.
Let us discuss the AWS security credentials in detail.
What is AWS Access Key ID and Secret Access Key?
An AWS access key ID and secret access key are the primary forms of security credentials used for programmatic access to its services and resources. Each access key includes a unique identifier for user applications and its respective secret access key which is required to sign requests to AWS services.
Let us learn how to create and manage access keys.
Create and Manage Access Keys
Access keys can be created and managed in AWS Identity and Access Management (IAM) console or AWS Command Line Interface (CLI). Multiple access keys may be issued per user to ensure increased security.
Let us learn the best practices for using these access keys.
What are the Best Practices to Use the Access Keys?
Below are given the best practices to use the access keys:
Let us learn more about these practices.
Revolve Access Keys Regularly
To reduce the impact of unauthorized entry and prevent potential breaches and threats in security, it is wise to rotate access keys from time to time.
Avoid Hardcoding Access Keys
Access keys should never be hardcoded into applications or stored in source code repositories. These can be exposed and cause vulnerability for your account.
IAM User Credentials
IAM users are entities within an AWS account that represent individuals or applications requiring access to AWS resources. An IAM user can possess login credentials (username/password or programmatic keys) for console use or programmatic keys for programmatic usage.
Let us learn how to create and manage IAM Users.
Create and Manage IAM Users
IAM users can be created, managed, and given permissions through either its console or API. IAM accounts should be created according to the principle of least privilege. It means to only assign those permissions that are necessary for the intended tasks.
IAM Roles
IAM roles function like IAM users but lack permanent credentials. Instead, they are assumed by trusted entities such as AWS services or external identities who take on temporary security credentials for that role. The below figure gives a basic understanding of IAM Roles:
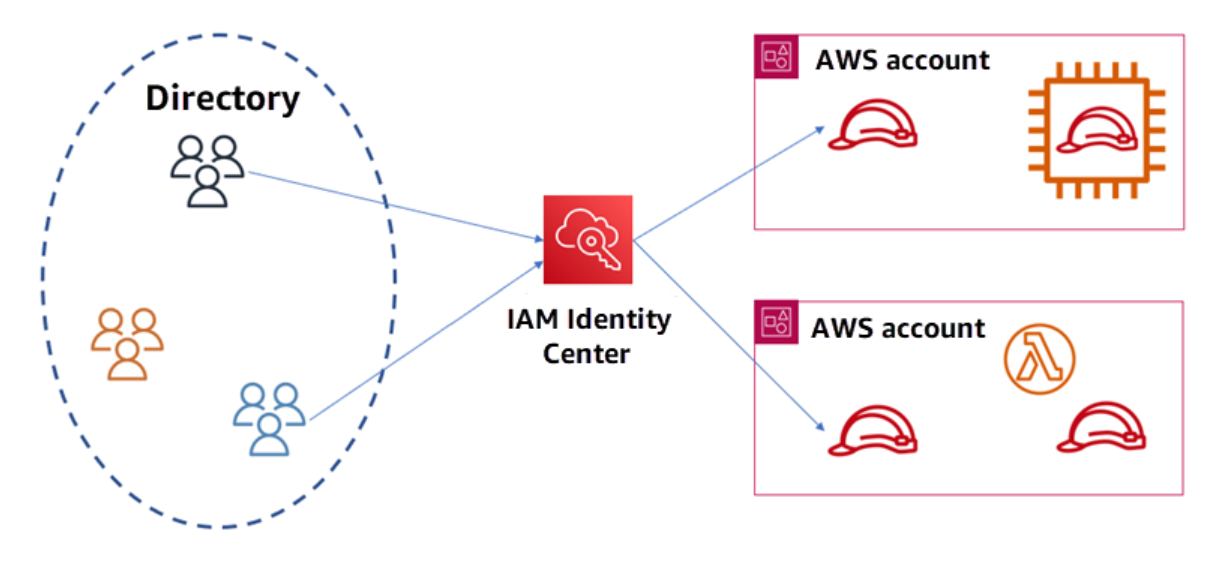
Let us learn how to create and manage IAM Roles.
Create and Manage IAM Roles
IAM roles can be created and managed using either its console or API.
Security Token Service (STS) Tokens
AWS Security Token Service (STS) offers temporary credentials called STS tokens that allow access to AWS resources. STS tokens can be acquired either by taking on an IAM role or through external identity providers like Amazon Cognito or Active Directory federating access.
Let us learn how to create and manage STS Tokens.
Create and Manage STS Tokens (STS Tokens)
STS tokens can be acquired using API calls to AWS STS service and then utilized by applications as temporary credentials to gain secure access to AWS services and resources.
X.509 Certificates
AWS makes use of X.509 certificates as part of their secure communications services, especially Identity and Access Management (IAM) and Key Management Service (KMS). These certificates allow services like IAM/KMS to sign requests, authenticate users, encrypt data securely, sign requests, sign requests from clients as well as sign documents if needed.
Let us learn how to create and manage X.509 Certificates.
Create and Manage X.509 Certificates
X.509 certificates can be generated using tools such as OpenSSL or purchased directly from certificate authorities. AWS services like IAM, KMS, and the ACM manage and use these certificates.
Conclusion
AWS security credentials are critical components in safeguarding interactions with AWS resources. Each service and protocol has its own specific function and management techniques. Best practices such as regular rotation, hardcoding avoidance, and following the least privilege are integral parts of creating and managing a safe AWS environment.
Source: linuxhint.com
